Two factor authentication setup on Wordfence sets the stage for significantly boosting your WordPress website’s security. This detailed guide explores the process, from understanding the fundamental concept of 2FA to implementing it seamlessly within Wordfence, a popular security plugin. We’ll cover various methods, configurations, and troubleshooting steps to ensure a robust and secure setup for your site.
Imagine effortlessly adding an extra layer of protection to your WordPress site. That’s the power of 2FA. This guide simplifies the process, providing a clear roadmap to enhance your site’s defenses against unauthorized access. We’ll break down the technicalities into easily digestible steps, making the entire setup process intuitive and straightforward.
Introduction to Two-Factor Authentication (2FA)

Two-factor authentication (2FA) adds an extra layer of security to your WordPress website, making it significantly harder for hackers to gain unauthorized access. Think of it as requiring a key and a code, instead of just a key. This added security is crucial in today’s digital landscape where cyber threats are ever-present.FA works by requiring two different verification methods to confirm your identity.
This significantly reduces the risk of unauthorized access, even if a hacker manages to obtain your password. This is because they need to gain access to more than one authentication method to log in. This layered approach is a powerful defense against common hacking tactics.
Understanding the Concept of 2FA
FA essentially verifies your identity in two distinct ways. One factor is typically something you know (like a password), and the other is something you possess (like a unique code from an authenticator app). This combination makes it far more difficult for unauthorized individuals to access your account.
How 2FA Works
The process usually begins with a successful login attempt using your username and password. This is the first factor. Then, a second verification method is initiated. This could be receiving a code via SMS, an authenticator app, or an email. You then enter this code to complete the login process.
This second factor ensures only authorized users gain access.
Benefits of Using 2FA for WordPress Websites
Implementing 2FA on your WordPress website significantly enhances security. It creates a formidable barrier against unauthorized access attempts. This added protection is especially crucial given the vulnerability of websites to various attacks, such as brute-force attacks and credential stuffing. This robust approach protects your site and user data.
Examples of Different 2FA Methods
Various methods are available to implement 2FA. Common options include receiving a code via email, SMS text message, or authenticator apps. These methods provide diverse security options tailored to individual preferences and security needs.
Comparison of 2FA Methods
| Method | Description | Pros | Cons |
|---|---|---|---|
| A code is sent to your registered email address. | Widely available, often already configured. | Reliance on email service, potential for spam/phishing. | |
| SMS (Text Message) | A code is sent to your mobile phone number. | Convenient, widely accessible. | Potential for SIM swapping attacks, carrier issues. |
| Authenticator Apps (e.g., Google Authenticator) | Generate time-based one-time passwords. | Highly secure, less susceptible to interception. | Requires a dedicated app, potentially less convenient. |
Wordfence Integration with 2FA
Wordfence, a popular WordPress security plugin, significantly enhances website security by providing robust 2FA integration. This allows website owners to add an extra layer of protection against unauthorized access, safeguarding sensitive data and maintaining the integrity of their online presence. Leveraging 2FA with Wordfence can drastically reduce the risk of account compromise and subsequent data breaches.Wordfence seamlessly integrates with various 2FA providers, offering a flexible and customizable approach to bolstering website security.
This integration streamlines the 2FA setup process, reducing the complexity often associated with implementing multiple plugins. The streamlined approach ensures that website owners can quickly and easily implement strong security measures without significant technical overhead.
Supported 2FA Plugins
Wordfence supports several leading 2FA plugins. This broad integration ensures compatibility with a wide range of user preferences and technical setups. This means that users can choose the 2FA method that best suits their needs and technical expertise.
- Google Authenticator: A widely used and highly regarded 2FA app, Google Authenticator is a popular choice for its ease of use and reliability. Its compatibility with Wordfence ensures a smooth and secure setup process.
- Authy: Another prominent 2FA provider, Authy provides a robust platform for managing multiple 2FA accounts. Wordfence’s integration with Authy allows for secure access management across various online platforms.
- FreeOTP: A free and open-source OTP (One-Time Password) generator, FreeOTP is a valuable alternative for users seeking a cost-effective and open-source solution. Wordfence’s support for FreeOTP simplifies the setup process for users preferring this approach.
- Other compatible providers: Wordfence often integrates with other 2FA solutions, expanding the range of options available to website owners. This ensures users can leverage the most suitable 2FA solution for their specific needs and preferences.
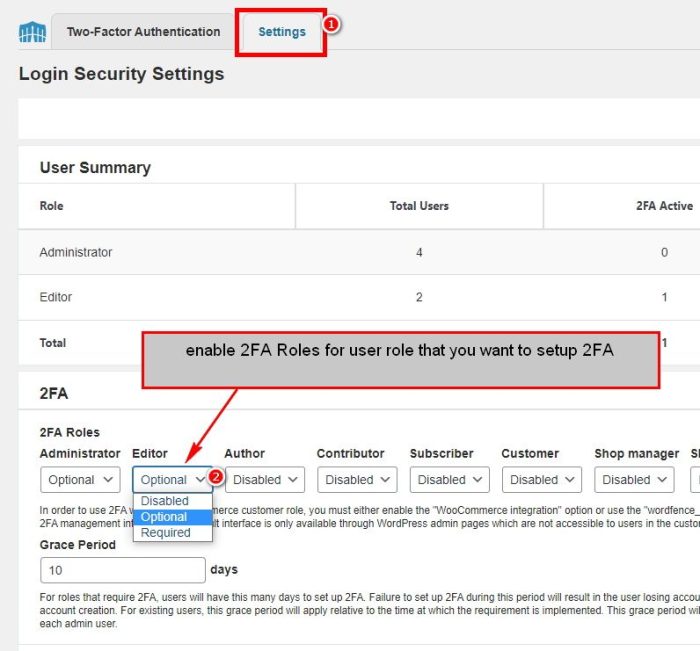
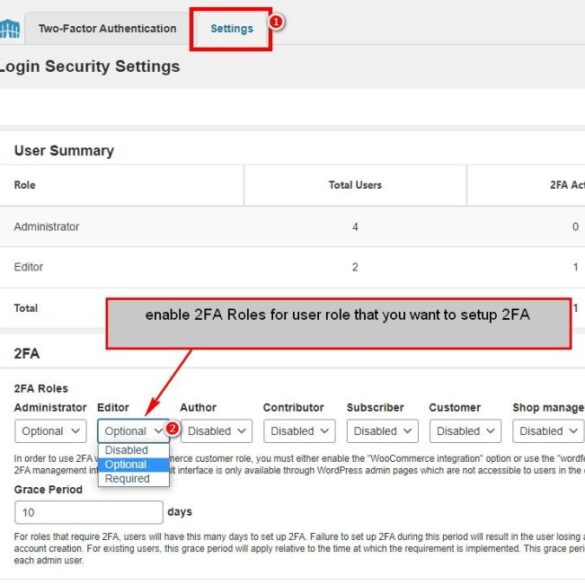
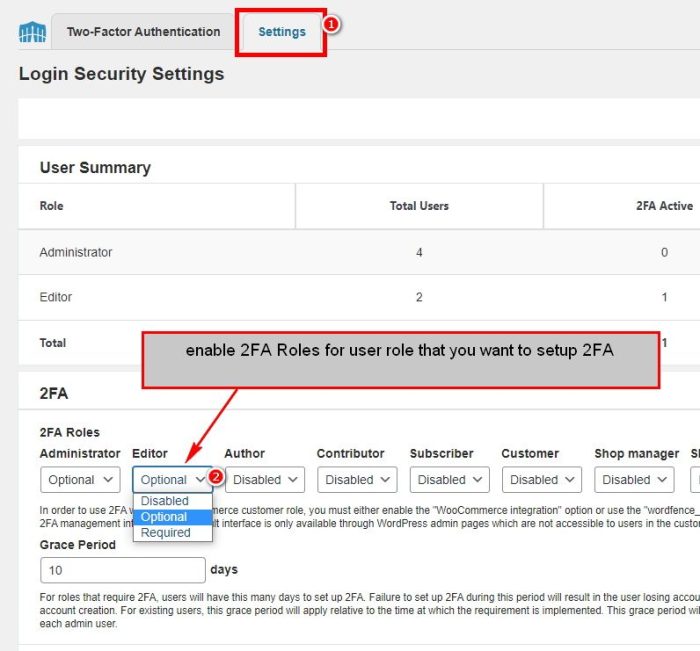
Enabling 2FA within Wordfence
Enabling 2FA within Wordfence is a straightforward process. The plugin provides clear instructions and intuitive interfaces, minimizing any potential difficulties during the setup process. It usually involves configuring the chosen 2FA provider and then linking it to the Wordfence account.
- Select the desired 2FA plugin from the available options within the Wordfence settings.
- Follow the specific setup instructions provided by the chosen plugin. These instructions will usually guide you through the authentication process and the creation of a backup code.
- Enter the required details for your 2FA provider (e.g., app code or scanning a QR code). This step varies slightly depending on the provider.
- Confirm the setup by completing any necessary verification steps.
Security Improvements
Implementing 2FA through Wordfence significantly enhances the overall security posture of a website. It adds an extra layer of protection, making it considerably harder for unauthorized individuals to gain access to user accounts. This additional layer of protection can be crucial in preventing malicious actors from gaining control of the website.
Using 2FA significantly reduces the risk of account takeover and data breaches, a critical aspect of maintaining online security.
Configuring 2FA on Wordfence
| Step | Action |
|---|---|
| 1 | Access Wordfence settings and navigate to the 2FA section. |
| 2 | Select the desired 2FA plugin from the available options. |
| 3 | Follow the plugin’s setup instructions to complete the integration process. |
| 4 | Enter the required details for the 2FA provider (e.g., app code or scanning a QR code). |
| 5 | Confirm the setup and complete any verification steps. |
Setting up 2FA on Wordfence
Two-factor authentication (2FA) adds an extra layer of security to your WordPress site by requiring a second verification method beyond your password. This enhances protection against unauthorized access, even if a hacker obtains your password. Wordfence’s 2FA integration allows you to implement this critical security measure seamlessly.Wordfence’s 2FA setup is straightforward and enhances your site’s overall security posture.
It offers various methods, allowing you to choose the one that best suits your needs and comfort level. This detailed guide will walk you through the process, from initial configuration to choosing a suitable 2FA application.
Wordfence 2FA Plugin Integration
Integrating a 2FA plugin into Wordfence typically involves activating the plugin within your WordPress dashboard. Wordfence often works seamlessly with popular 2FA plugins, enabling the functionality through its core interface.
Configuration Options Within Wordfence’s 2FA Setup
Wordfence’s 2FA configuration provides a range of customization options. These settings allow you to tailor the 2FA experience to your specific security requirements. You can choose the 2FA application you want to use, such as Google Authenticator or Authy.
Comparison of Wordfence 2FA Setups (e.g., Google Authenticator)
Different 2FA applications offer varying user experiences and security features. For example, Google Authenticator generates time-based one-time passwords (TOTP). This process is widely used and recognized for its effectiveness in securing online accounts. Other applications might offer similar functionalities with different interface designs or additional security features.
Steps for Setting Up 2FA with Wordfence
The following table Artikels the steps involved in setting up 2FA with Wordfence, using Google Authenticator as an example. Note that the exact steps might slightly vary depending on the specific version of Wordfence and the 2FA plugin being used.
| Step | Description | Screenshot Description |
|---|---|---|
| 1. Install and Activate the Wordfence Security Plugin. | Navigate to Plugins in your WordPress dashboard and search for “Wordfence.” Install and activate the plugin. | A screenshot showing the “Plugins” section of the WordPress dashboard with the installed and activated Wordfence plugin highlighted. |
| 2. Access Wordfence Settings. | Once activated, access the Wordfence settings page. | A screenshot showing the Wordfence settings page, which is usually accessible from the Wordfence menu in your WordPress dashboard. |
| 3. Enable 2FA. | Locate the 2FA section within the Wordfence settings. Enable 2FA by checking the appropriate box. | A screenshot of the Wordfence settings page, highlighting the 2FA toggle. |
| 4. Choose Your 2FA Application. | Select your preferred 2FA application (e.g., Google Authenticator). This step usually involves scanning a QR code or entering a unique secret key. | A screenshot showing the 2FA application selection screen, possibly including a QR code for scanning with your authenticator app. |
| 5. Configure Your Chosen Application. | Use your chosen 2FA application to scan the provided QR code or enter the secret key. This will generate a one-time passcode for initial verification. | A screenshot showing the Google Authenticator app with the scanned QR code or the secret key displayed. |
| 6. Enter the Verification Code. | Enter the one-time passcode generated by your 2FA application into the designated field within Wordfence settings. | A screenshot of the Wordfence settings page, showing the input field for the verification code. |
| 7. Verify and Confirm. | Verify the configuration by confirming the setup. | A screenshot of the Wordfence settings page, showing a confirmation message or a successful setup notification. |
Security Considerations for 2FA
Two-factor authentication (2FA) significantly strengthens online security by requiring two forms of verification. This adds a crucial layer of protection beyond just a password, making it much harder for unauthorized individuals to access your accounts. However, even with 2FA, potential security risks exist. Understanding these risks and implementing appropriate safeguards is paramount to maximizing the benefits of this enhanced security measure.Implementing 2FA is a proactive step, but neglecting crucial security aspects can negate its effectiveness.
Setting up two-factor authentication on Wordfence is a smart move for boosting security. It’s a crucial step, especially after reading about the incredible success story of Kendra Cannoy, a rising star in the SEO world. Kendra Cannoy’s journey highlights the importance of robust online protection, and a well-configured two-factor authentication system is a cornerstone of that protection.
Implementing this on your Wordfence setup will definitely help you sleep soundly at night.
Proper configuration and diligent adherence to security best practices are essential to ensure 2FA works as intended and doesn’t become a weakness.
Potential Security Risks Related to 2FA Setup
Implementing 2FA correctly is essential to avoid security vulnerabilities. Incorrect setup or inadequate understanding of the process can create unintended security risks. Choosing a reputable 2FA provider and configuring the system correctly is crucial.
Importance of Strong Passwords and 2FA Codes
Strong passwords and robust 2FA codes are fundamental to protecting your accounts. A weak password combined with a 2FA system can still be compromised. A strong password, ideally a complex mix of uppercase and lowercase letters, numbers, and symbols, coupled with a secure 2FA method, significantly strengthens your security posture. Never reuse passwords across multiple accounts. Regularly updating passwords and using a password manager are also crucial.
2FA codes should be treated as confidential information and not shared.
Handling Lost or Compromised 2FA Devices
Losing or having a 2FA device compromised can lead to account lockout. Immediately disable any compromised devices and change associated passwords. Review account settings for recovery options. Consider implementing multi-factor authentication (MFA) for added security. Contacting support is often the first step if you suspect a breach or lose your device.
Common 2FA Security Vulnerabilities
Phishing attempts are a major concern. Attackers frequently target 2FA codes by tricking users into revealing them. Social engineering tactics, such as fake websites mimicking legitimate login pages, are used. Unsecure Wi-Fi networks and unpatched software can expose your 2FA devices to compromise. Always verify the legitimacy of requests for 2FA codes.
Be wary of suspicious emails or messages.
Protecting Against Phishing Attempts Targeting 2FA
Phishing attacks are a significant threat to 2FA security. Verify the source of all requests for 2FA codes. Look for inconsistencies in the email or website address. Never click on suspicious links or download attachments from unknown sources. Educate yourself on common phishing tactics to better recognize and avoid these attacks.
Secure Storage and Management of 2FA Credentials
Securely storing and managing 2FA credentials is crucial. Do not write down 2FA codes or store them in insecure locations. Use a reputable password manager for secure storage and retrieval of sensitive information. Never share your 2FA credentials with anyone. Enable two-step verification for your accounts to prevent unauthorized access.
Setting up two-factor authentication on Wordfence is crucial for website security. Recent Google updates to their site reputation abuse policy documentation highlight the importance of robust security measures. These updates, detailed in the google updates site reputation abuse policy documentation , underscore how crucial it is to protect your site from malicious activity. Implementing two-factor authentication remains a vital step in bolstering your site’s defenses.
Troubleshooting 2FA Setup: Two Factor Authentication Setup On Wordfence
Two-factor authentication (2FA) significantly enhances website security by requiring a second verification step beyond a password. However, occasional issues can arise during setup. This section details common problems and their solutions, ensuring a smooth and secure 2FA implementation.
Common 2FA Setup Issues
Troubleshooting 2FA setup involves identifying and resolving various problems. These issues range from incorrect app configurations to connection errors. Understanding these potential roadblocks allows for quick and effective solutions.
Incorrect App Configuration
Misconfigurations in the 2FA application (e.g., incorrect account details, missing setup steps) are common problems. Ensure your 2FA app is correctly integrated with your Wordfence account and that all required steps in the setup process are completed. Verify the app’s compatibility with your operating system and device.
Connection Problems
Network connectivity issues, such as poor internet connections or firewall restrictions, can hinder the 2FA setup process. Check your internet connection and ensure your firewall doesn’t block the required communication channels. Temporary network outages can also cause connection problems; try again later if this is the case.
Device Compatibility Issues
Problems may arise if your device isn’t compatible with the chosen 2FA app. Verify the app’s compatibility with your operating system and device model. Ensure the device’s time and date settings are accurate, as they can sometimes impact the 2FA process.
Setting up two-factor authentication on Wordfence is crucial for website security. It’s a small step that can dramatically boost your online protection. Just like being fearless in content creation, you need to embrace the challenge of bolstering your online presence. Be fearless in content creation and similarly, don’t be afraid to take proactive steps like enabling two-factor authentication on Wordfence.
This extra layer of security can save you from unwanted intruders and ensure your website remains safe and sound.
Recovery of Lost 2FA Credentials
Losing your 2FA credentials can lead to account lockouts. If this happens, contact Wordfence support immediately. They can provide instructions on recovering your account and resetting your 2FA credentials. Before contacting support, ensure you have documented your 2FA setup details, including the recovery options you may have set up.
Troubleshooting Table
| Problem | Solution |
|---|---|
| Incorrect app configuration | Verify account details, complete all setup steps, check app compatibility, and ensure proper integration with Wordfence. |
| Connection problems | Check internet connection, ensure firewall doesn’t block communication channels, and try again later if there’s a temporary outage. |
| Device compatibility issues | Verify app compatibility with your device and operating system. Ensure accurate time and date settings on your device. |
| Lost 2FA credentials | Contact Wordfence support immediately for instructions on recovering your account and resetting your 2FA credentials. |
Advanced 2FA Configurations
Two-factor authentication (2FA) significantly enhances website security, but sometimes standard configurations aren’t enough. Wordfence’s 2FA allows for advanced customization, enabling administrators to tailor the system to their specific needs. This section delves into the advanced features, custom configurations, and integration of custom 2FA methods within the Wordfence platform.Wordfence’s advanced 2FA features provide a robust framework for security beyond basic authentication.
Administrators can fine-tune security policies, enabling greater control over user access and system protection.
Custom Configurations for 2FA Settings
Wordfence allows for the tailoring of 2FA settings to accommodate diverse security requirements. Customizing the authentication flow can be achieved through various settings, ensuring compatibility with different user needs and risk tolerances. This includes setting thresholds for authentication attempts, defining time-based windows for code validity, and adjusting notification methods. The level of customization can be considerable, ensuring that each user’s security profile can be uniquely addressed.
Integrating Custom 2FA Methods, Two factor authentication setup on wordfence
While Wordfence integrates with common 2FA providers, integrating custom methods may be necessary for specific use cases. This process often involves creating custom plugins or extensions to adapt to unique authentication protocols. The process is not trivial, requiring in-depth understanding of both the custom method and Wordfence’s API. Careful consideration of security implications is crucial in this process, to prevent vulnerabilities.
Advanced 2FA Scenarios
Advanced 2FA scenarios demonstrate the versatility of the system. One example is implementing multi-level authentication, where users need to satisfy multiple 2FA criteria before accessing sensitive data. Another scenario might involve requiring different 2FA methods for different types of actions. For example, a user might need a one-time code for login, but a biometric scan for making substantial financial transactions.
These tailored configurations ensure a layered approach to security.
Comparison of Advanced 2FA Options
| Feature | Time-Based One-Time Passwords (TOTP) | Biometric Authentication | Push Notifications | SMS/Email Verification |
|---|---|---|---|---|
| Security | High, if properly implemented | Very high, depending on the system | Medium, if secured | Medium, if secured |
| User Experience | Good, familiar method | Good, convenient for frequent users | Good, convenient | Good, widely used |
| Cost | Low | Variable, depending on the implementation | Low | Low |
| Complexity | Low | Medium | Low | Low |
This table provides a concise overview of common advanced 2FA options. Choosing the right method depends on the specific security needs and the technical capabilities of the system.
Best Practices for 2FA
Two-factor authentication (2FA) significantly enhances online security by adding an extra layer of verification beyond a simple password. Implementing 2FA best practices is crucial for protecting your accounts and sensitive data from unauthorized access. This comprehensive guide will cover selecting appropriate 2FA methods, illustrating good and bad practices, and outlining a step-by-step implementation strategy.Properly implementing 2FA not only strengthens your defenses against hackers but also protects your personal and financial information from theft.
A well-structured 2FA strategy significantly reduces the risk of account compromise, even if a hacker manages to obtain your password.
Selecting 2FA Methods
Choosing the right 2FA method is paramount. Different methods offer varying levels of security and convenience. Factors to consider include ease of use, reliability, and potential vulnerabilities. Methods like SMS-based codes, authenticator apps, and hardware tokens each have unique characteristics that affect their suitability for different users and situations.
- SMS-based codes are convenient but vulnerable to SIM swapping attacks. Their reliance on cellular networks makes them susceptible to interception or manipulation.
- Authenticator apps offer a more secure alternative, using time-based one-time passwords (TOTP). These codes are generated locally and are less susceptible to network-based attacks.
- Hardware tokens provide the highest level of security. These physical devices generate unique codes without relying on internet connections, making them resistant to many attack vectors.
Examples of Good and Bad 2FA Practices
Understanding the difference between good and bad 2FA practices is vital for effective implementation. A robust strategy involves carefully selecting methods and consistently applying them across all accounts.
- Good practice: Using an authenticator app for most accounts and a hardware token for high-value or sensitive accounts. This multi-layered approach significantly increases security.
- Bad practice: Relying solely on SMS-based codes for all accounts, leaving your accounts vulnerable to SIM swapping attacks.
- Bad practice: Using the same password and 2FA secret for multiple accounts. This creates a single point of failure if one account is compromised.
Implementing 2FA Best Practices
A step-by-step approach to implementing 2FA best practices is essential for successful security reinforcement. Each step should be carefully considered to avoid potential vulnerabilities.
- Choose appropriate methods: Carefully evaluate your needs and select methods that balance security and convenience. For critical accounts, use hardware tokens. For everyday accounts, consider authenticator apps.
- Configure 2FA: Follow the instructions provided by each service provider to set up 2FA. This includes downloading authenticator apps and configuring hardware tokens.
- Enable 2FA: Activate 2FA for all accounts that support it. This should include email accounts, banking platforms, and social media accounts.
- Store backup codes: Generate and store backup codes securely. These codes are essential for regaining access if you lose your primary device or access to your authenticator app.
- Regularly review and update: Regularly review your 2FA settings to ensure they remain effective and aligned with current security best practices.
Best Practices Summarized
Implementing strong 2FA practices is a proactive measure to protect your online accounts and personal information. A multi-layered approach, encompassing different authentication methods, significantly enhances security.
- Use a combination of authentication methods.
- Never reuse passwords or 2FA secrets across different accounts.
- Store backup codes securely in a physical or digital vault.
- Regularly review and update 2FA settings.
- Choose methods based on security and convenience.
Outcome Summary
In conclusion, securing your WordPress site with two-factor authentication (2FA) using Wordfence is a crucial step in today’s digital landscape. This guide has provided a comprehensive overview, from the basics of 2FA to advanced configurations and troubleshooting. By following the steps Artikeld, you can significantly improve your site’s security posture. Remember, a well-configured 2FA system is a powerful defense against potential threats.