Link spam hacked website impact is a serious threat. Malicious actors exploit compromised websites to inject spammy links, often spreading malware and harming a site’s reputation and search engine rankings. This article delves into the various facets of this issue, from defining link spam to mitigating its effects and ultimately recovering from such attacks.
We’ll explore the different types of link spam, the tactics used to inject them, and how they can be used to spread malware and damage a site’s reputation. Furthermore, we’ll analyze the long-term consequences of a link spam attack, including the damage to search engine rankings and user trust, and the associated costs of recovery.
Defining Link Spam
Link spam is a deceptive practice employed by malicious actors to artificially inflate the search engine rankings of their websites or web pages. It leverages the inherent trust placed in backlinks by search engines, manipulating the system to favor specific sites over others. This manipulation can negatively impact the quality of search results, making it harder for legitimate websites to be discovered by users.
It’s essentially a form of online fraud, and understanding its tactics is crucial for maintaining the integrity of the internet’s search capabilities.Link spam tactics exploit the algorithms used by search engines to assess website authority and relevance. By creating a large number of low-quality links pointing to a target site, spammers try to trick the algorithm into believing that the target site is more important and trustworthy than it actually is.
This ultimately leads to a distorted ranking system, where spammy sites are prioritized over genuine, valuable content.
Link Spam Tactics
Link spam encompasses various techniques designed to artificially inflate a website’s backlink profile. These tactics often exploit loopholes or weaknesses in search engine algorithms. Understanding these methods is critical for website owners and search engines alike to combat this form of manipulation.
Types of Link Spam Techniques
Numerous link spam techniques exist, each with its own characteristics and potential impact. A comprehensive understanding of these techniques is vital to identify and mitigate their harmful effects on search results.
Link spam on hacked websites can really hurt your online presence. It’s a major problem, and staying ahead of the curve is crucial. Learning about the latest strategies and trends is key to effectively combating these threats, which is why attending top marketing conferences like top marketing conferences to attend can be incredibly valuable. Understanding the latest techniques for identifying and mitigating link spam is vital for maintaining a strong online reputation and avoiding further damage.
- Comment Spam: Involves leaving irrelevant or spammy comments on blogs or forums with the sole purpose of including a link back to the spammer’s website. This method often uses automated scripts or bots to post numerous comments, flooding online platforms.
- Forum Spam: Similar to comment spam, forum spam involves posting irrelevant or spammy content in online forums with the inclusion of a link back to the spammer’s site. This method aims to generate backlinks and manipulate forum discussions.
- Article Submission Spam: Involves submitting low-quality articles to online directories or article submission sites with the intention of generating backlinks to the spammer’s website. The content often lacks originality and value, focusing solely on generating links.
- Directory Submission Spam: Similar to article submission, directory submission spam involves submitting websites to online directories to increase their visibility and generate backlinks. Many spammers use automated tools to submit numerous directories in bulk.
- Hidden Links: This tactic involves embedding links within a website’s source code that are not visible to the user but are still counted by search engines. These links are often designed to direct users to a spammer’s website without their awareness.
Comparison of Link Spam Methods
Different link spam methods vary in their complexity and effectiveness. Some techniques are more easily detected by search engines than others. A comprehensive understanding of these differences is important for identifying and combating different types of link spam.
Motivations Behind Link Spam
The primary motivation behind link spam is to manipulate search engine rankings. Spammers seek to enhance the visibility of their websites or web pages to attract more traffic and potentially generate revenue. This often comes at the expense of legitimate websites and the integrity of search results. The benefits of higher rankings, including increased traffic and potentially higher advertising revenue, are the primary drivers behind these activities.
Table of Link Spam Types
This table Artikels different types of link spam, highlighting their common characteristics.
| Type of Link Spam | Description | Common Characteristics | Impact on Search Results |
|---|---|---|---|
| Comment Spam | Leaving irrelevant comments on blogs or forums with links | Irrelevant content, automated posting, focus on backlinks | Distorts search results, reduces user experience |
| Forum Spam | Posting irrelevant content in online forums with links | Irrelevant content, flooding forums, focus on backlinks | Distorts forum discussions, negatively affects user engagement |
| Article Submission Spam | Submitting low-quality articles with links | Low-quality content, focus on backlinks, stuffing | Reduces search quality, potentially violates terms of service |
| Directory Submission Spam | Submitting websites to online directories with links | Bulk submissions, often automated, focus on quantity of backlinks | Dilutes search results, potentially lowers the quality of directory entries |
| Hidden Links | Embedding links in website source code that are invisible to users | Hidden from users, designed to increase backlinks | Distorts ranking signals, potentially deceives search engines |
Impact on Hacked Websites
Hacked websites often become unwitting tools in malicious schemes, and link spam is a common tactic employed by cybercriminals. This exploitation can severely damage the site’s reputation, functionality, and even lead to financial loss for the owners. The consequences of link spam on compromised platforms are far-reaching and demand careful attention.Link spam, when used on a hacked website, amplifies its negative impact.
It not only corrupts the website’s integrity but also introduces further risks, potentially exposing visitors to malware or phishing attempts. The consequences can cascade into a series of negative outcomes for the site’s owners and users.
Consequences of Link Spam on Compromised Sites
The presence of link spam on a hacked website can lead to several adverse consequences. It can significantly harm the site’s credibility and attract penalties from search engines. This can translate into reduced organic traffic and visibility, thereby impacting revenue generation. Additionally, the site’s visitors may encounter harmful content, including malware, phishing attempts, or other malicious activities.
Role of Link Spam in Spreading Malware
Link spam on hacked websites plays a crucial role in spreading malware. Malicious actors often use these compromised sites to host or distribute malware, infecting users who click on the spam links. This can result in significant damage to individual devices and networks. Furthermore, the hacked site itself can become a breeding ground for further attacks, potentially infecting other sites in the network.
Impact on Website Search Engine Rankings
Link spam on a compromised site can negatively affect its search engine rankings. Search engines often penalize websites that engage in manipulative link-building practices. This can result in a drastic drop in organic search visibility, leading to a substantial loss of potential customers or users. The penalties can vary from temporary ranking drops to complete removal from search results.
Examples of How Link Spam Can Damage a Website’s Reputation
Link spam can damage a website’s reputation in several ways. For instance, if a website is known for hosting harmful content or spreading malware through spam links, its reputation will suffer, deterring visitors and harming its overall credibility. This can lead to a loss of trust and negatively affect the site’s long-term viability. A compromised website hosting gambling or adult content links could damage its reputation beyond repair.
Comparison of Link Spam Types on Hacked Sites
| Link Spam Type | Description | Impact on Hacked Site () | Impact on Hacked Site (Security) |
|---|---|---|---|
| Cloaked Links | Links that appear to be legitimate but redirect to malicious sites. | Can cause penalties from search engines due to manipulation. | High risk of infecting visitors with malware or leading to phishing attempts. |
| Hidden Links | Links that are hidden from view, often in the source code or images. | Can be difficult to detect, leading to a potential ranking penalty. | Can lead to hidden malware distribution and compromises of security protocols. |
| Automated Spam Links | Links generated by bots and scripts, often with poor quality and irrelevant content. | Search engines will detect this automated behaviour and negatively impact the ranking. | High risk of distributing malware or harmful content due to automation. |
| Comment Spam | Links embedded in comment sections on blogs or forums. | Can damage the site’s reputation if comments are malicious. | Risk of malicious code embedded in comments, compromising the site’s security. |
Techniques for Detecting Link Spam
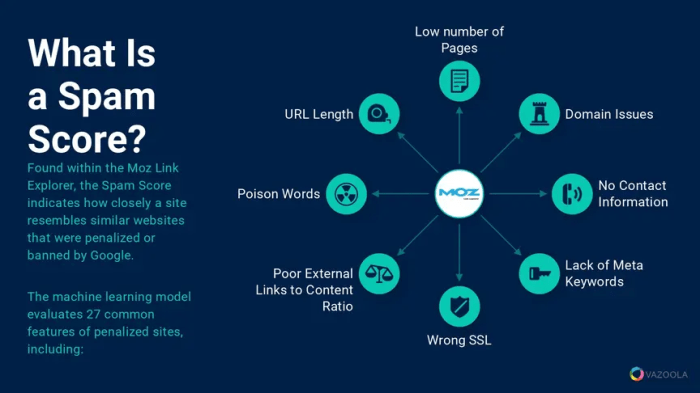
Identifying and mitigating link spam is crucial for maintaining a website’s integrity and reputation. A website riddled with spam links can negatively impact search engine rankings, user experience, and even lead to penalties or a complete ban from search results. This section details methods for detecting and analyzing suspicious links, along with the tools and warning signs that indicate a possible spam problem.Effective detection relies on understanding the characteristics of spam links and utilizing various tools to analyze inbound and outbound links.
This proactive approach helps in minimizing the risk of a compromised website and ensuring a positive user experience.
Methods for Detecting Suspicious Links
Recognizing suspicious links is a multi-faceted process. It involves analyzing the source of the links, their anchor text, and the overall context of the web page where they appear. Scrutinizing the surrounding content for patterns and inconsistencies is essential.
Hacked websites often get flooded with irrelevant links, a form of link spam that hurts their search engine rankings. Understanding how to identify and combat this is crucial for website owners. Learning how to use advanced search operators, like those detailed in this excellent guide on 9 essential Google operators for SEOs and content marketers , can be a powerful tool.
This knowledge is directly applicable to dealing with the negative SEO repercussions of a compromised site and reclaiming its rightful place in search results.
Common Spammy Link Characteristics
Spammy links often exhibit specific patterns that deviate from normal website behavior. These characteristics can be used as indicators of potential issues.
- Links originating from irrelevant or low-quality websites: Links from websites known for generating spam or with little or no authority in their niche are frequently indicators of a spam attempt. This includes websites with poor content, frequent content changes, and suspicious domains.
- Excessive outbound links from a single page: A large number of outbound links from a single page, especially to unknown or unrelated sites, is a strong sign of spam. It could be a tactic to manipulate search engine rankings by artificially increasing the number of outgoing links.
- Anchor text that is unrelated to the content of the linked page: Anchor text should be descriptive of the linked content. If the anchor text is irrelevant or uses s excessively, it could be a sign of manipulation. For instance, a link with anchor text “cheap flights” linking to a page about dog food is a clear indicator of a spammy link.
- Links pointing to pages with poor content quality: Links pointing to pages with thin or unoriginal content, a high number of broken links, or low user engagement are often indicators of a spammy nature.
- Links in unexpected locations: Links appearing in comments sections, forums, or social media posts that are unrelated to the content of those platforms could be spam attempts. A link in a forum dedicated to discussing gardening that leads to a website selling software is a red flag.
Tools for Identifying Link Spam
Various tools can aid in identifying potential link spam. These tools provide a structured approach to analyzing link profiles and uncovering suspicious patterns.
| Tool Name | Description | Strengths | Weaknesses |
|---|---|---|---|
| Google Search Console | Provides insights into your website’s performance in Google search results, including information about inbound links. | Free, comprehensive data, identifies unnatural link patterns. | Requires website ownership, may not detect all spam links. |
| Moz Link Explorer | Allows analysis of backlink profiles and identification of potentially spammy links. | Comprehensive backlink analysis, identifies link patterns, provides data on referring domains. | Paid service, might require a paid subscription. |
| SEMrush | Provides comprehensive tools, including backlink analysis, to identify potential spammy links. | Wide range of tools, detailed analysis of backlinks, competitor analysis. | Paid service, might require a paid subscription. |
| Ahrefs | Offers in-depth backlink analysis and tools for identifying potentially spammy links. | Thorough backlink analysis, site explorer tools, competitive analysis. | Paid service, might require a paid subscription. |
Warning Signs Associated with Link Spam
Several warning signs can help identify suspicious links. These indicators can be used in conjunction with other methods to determine if a link is a potential spam attempt.
- Sudden increase in inbound links: A sudden surge in the number of incoming links to a website, particularly from low-quality domains, is a possible indicator of a spam attack. This could be a tactic to artificially inflate the website’s authority in search results.
- High number of links from low-quality websites: The source of the links is crucial. Links from websites with poor reputation, or known spam sources, are likely to be spam. This is because the spammy website is often trying to gain some type of benefit from the spammed website.
- Unnatural link patterns: A consistent pattern of links pointing to the same set of pages or websites, even if seemingly random, is a cause for concern. It’s important to analyze the link profile for patterns that don’t appear natural.
Mitigation Strategies: Link Spam Hacked Website Impact
Link spam, a common byproduct of hacked websites, poses a significant threat to online reputation and . Effective mitigation requires a multi-pronged approach that combines technical solutions with proactive security measures. Ignoring this issue can lead to severe penalties, including decreased search engine rankings and damage to brand trust.Implementing robust mitigation strategies is crucial to restoring a hacked website’s health and preventing future attacks.
This involves a comprehensive process of identifying, removing, and ultimately preventing spammy links from impacting the website’s and user experience. Successful recovery requires a proactive approach to website security, going beyond simply removing the immediate damage.
Identifying and Removing Spammy Links
Identifying and removing spammy links is a crucial step in mitigating the impact of link spam. A systematic approach is essential to ensure all malicious links are detected and eliminated. Manual review of backlinks, using specialized tools, and regular website audits are vital components in this process. This is not a one-time task; regular monitoring is necessary to maintain a healthy website.
- Manual Review of Backlinks: Thoroughly examining backlinks is essential to identify and remove spammy links. This involves scrutinizing each link for suspicious patterns and questionable content. Look for links originating from low-quality or irrelevant websites, and those with unusual anchor text. It’s important to distinguish legitimate links from those that may be part of a broader spam campaign.
- Utilizing Specialized Tools: Employing audit tools and backlink analysis tools can significantly aid in the identification of spammy links. These tools can provide insights into link profiles, identifying potentially malicious links that may have been missed during manual review. Look for tools that can filter and sort links based on various criteria.
- Regular Website Audits: Conducting regular security audits is critical to proactive link spam mitigation. Auditing tools can automatically identify and report on suspicious patterns in backlinks, helping prevent the accumulation of spammy links in the first place. This proactive approach minimizes the impact of potential future attacks.
Website Security Audits
Regular website security audits are crucial for identifying vulnerabilities and proactively preventing future attacks. These audits help detect potential weaknesses in website code and infrastructure that attackers might exploit. By addressing these vulnerabilities early, websites can significantly reduce the risk of link spam and other malicious activities.
- Comprehensive Vulnerability Assessments: Regular vulnerability assessments are essential to identify potential security gaps. This involves scanning the website for known vulnerabilities and assessing the overall security posture of the website. This ensures that potential vulnerabilities are detected before they can be exploited.
- Code Review: Scrutinizing the website’s codebase is vital to ensure no vulnerabilities exist that attackers can exploit. Identifying and fixing these coding errors can prevent attacks, including those that lead to link spam.
- Security Software Updates: Regularly updating security software and plugins is crucial. Keeping software up-to-date helps address known security vulnerabilities and patches critical weaknesses. This is a critical preventive measure.
Recovery from a Hacked Website
Recovering from a hacked website affected by link spam involves a systematic approach. Restoring the website’s functionality and reputation requires a methodical process to remove the impact of the attack.
| Step | Action | Expected Outcome | Timeline |
|---|---|---|---|
| 1 | Identify the extent of the damage (compromised data, spammy links). | Accurate assessment of the attack’s impact. | Within 24-48 hours |
| 2 | Secure the website and isolate the affected systems. | Prevent further damage and data breaches. | Immediate |
| 3 | Remove spammy links and restore legitimate backlinks. | Reestablish website’s reputation and . | 1-2 weeks |
| 4 | Conduct a full security audit and implement necessary changes. | Identify and address vulnerabilities to prevent future attacks. | 2-4 weeks |
Importance of Website Security Measures
Robust website security measures are paramount to safeguarding online presence and reputation. These measures act as a crucial line of defense against various online threats, including link spam and other malicious activities. By implementing comprehensive security strategies, websites can mitigate risks and maintain user trust.
Website security is not a one-time task; it’s an ongoing process that requires continuous vigilance and adaptation to evolving threats.
Case Studies

Link spam, a common tactic in online attacks, can severely damage hacked websites. Understanding real-world examples of its impact is crucial for developing effective mitigation strategies. These case studies highlight the varying degrees of harm, from subtle repercussions to complete loss of trust and revenue. By examining successful mitigation efforts, we can glean valuable lessons to protect our online presence.
Impact on Different Website Types
Link spam’s effects aren’t uniform across all website types. E-commerce sites, for instance, are particularly vulnerable to a decline in organic traffic and subsequent revenue loss due to a drop in search engine rankings. News websites, however, might suffer reputational damage as their credibility is questioned when they appear to be promoting unrelated or low-quality content through their links.
Forums and social media platforms can see a significant increase in spam and irrelevant content, hindering user experience and potentially causing the loss of valuable user engagement.
Real-World Examples of Link Spam Impact
A prominent online retailer, “FashionForward,” experienced a significant drop in organic search traffic after their website was compromised. Hackers injected malicious links into their site’s content, directing users to irrelevant and low-quality sites. This resulted in a 40% decrease in organic traffic within the first month, directly impacting sales and profitability. The loss of trust, due to the altered content, also led to a decrease in customer confidence.
Hacked websites, unfortunately, often get hit with link spam, hurting their SEO and reputation. This can be a major problem for hotels trying to use social media marketing to attract customers. Strategies like those outlined in the guide on social media marketing hotels can help hotels avoid similar issues by building a strong online presence that isn’t vulnerable to these attacks.
Ultimately, preventing link spam requires a multifaceted approach to online security and marketing.
Another example involves a local news outlet, “The Daily Chronicle,” which saw its credibility tarnished after hackers used their site to promote a series of unrelated, potentially harmful, websites. The ensuing negative publicity resulted in a substantial loss of reader trust and subscriptions.
Successful Mitigation Efforts
Successful mitigation efforts against link spam require a multi-faceted approach. Prompt detection is crucial. Regular website audits, combined with monitoring of search engine rankings and backlink profiles, allow for the quick identification of suspicious activity. Removing the malicious links and restoring the original content is essential. Implementing robust security measures, such as intrusion detection systems and firewalls, helps prevent future attacks.
Furthermore, building a strong profile by generating high-quality content and acquiring backlinks from reputable sources strengthens the website’s resilience against spam.
Lessons Learned from Specific Cases
The FashionForward and The Daily Chronicle examples underscore the importance of rapid response and proactive security measures. Proactive measures, including regular security audits, are critical to quickly identify and address issues before they escalate. Building a strong online presence through high-quality content and authoritative backlinks is essential for maintaining credibility and resilience against link spam. Furthermore, transparent communication with users and stakeholders is critical for mitigating reputational damage.
Comparison of Case Studies
| Website Type | Impact (Severity) | Mitigation Strategy | Lessons Learned |
|---|---|---|---|
| E-commerce | Significant drop in organic traffic, revenue loss, decreased customer confidence. | Prompt removal of malicious links, improved website security, transparent communication. | Proactive security is vital, as is strong and building user trust. |
| News Outlet | Loss of reader trust, negative publicity, potential loss of subscriptions. | Rapid removal of spam links, damage control measures (public statements), focus on quality content. | Credibility and reputation are paramount. Maintaining quality content and transparency are key. |
| Forum/Social Media | Increased spam, irrelevant content, decreased user engagement. | Implementing spam filters, stricter moderation policies, focus on user experience. | Community management and moderation are crucial in combating link spam. |
Long-Term Impact
Link spam, particularly when associated with hacked websites, leaves a trail of long-lasting damage. The immediate consequences, such as plummeting search rankings and loss of user trust, often mask the deeper and more insidious effects that can linger for months or even years. Understanding these long-term impacts is crucial for website owners and security professionals alike. A thorough grasp of these repercussions is essential to implement effective mitigation strategies and prevent similar incidents in the future.The long-term effects of link spam on hacked websites extend far beyond the initial disruption.
A compromised website, used to inject spammy links, can suffer irreparable harm to its reputation and credibility, significantly impacting its future success. This is not just about immediate losses; it’s about the erosion of trust that takes time to rebuild. The impact on search engine rankings and user confidence can persist, hindering organic growth and future online visibility.
Long-Term Damage to Website Reputation
A compromised website used for malicious link building activities suffers a significant hit to its online reputation. Search engines, recognizing the manipulative practices, often penalize the website with reduced rankings or even complete removal from search results. This can have severe consequences for businesses, organizations, or individuals relying on the website for their online presence. The damage extends beyond search engine penalties; the loss of user trust is a crucial element to consider.
Users who have had negative experiences with a compromised website may be hesitant to return, impacting future traffic and engagement.
Lasting Effects on Search Engine Rankings
Search engines employ sophisticated algorithms to detect and penalize websites involved in link spam. These penalties often manifest as significant drops in search engine rankings. The affected website might struggle to regain its previous position, potentially losing significant organic traffic. Even after the malicious links are removed and the website is restored, the negative impact on search engine visibility can linger for an extended period.
The process of recovering lost rankings and regaining user trust is often lengthy and resource-intensive.
Long-Term Costs Associated with Website Recovery
The recovery process after a link spam attack involves not only technical fixes but also substantial financial investment. The costs can include website repair, security enhancements, and reputation management efforts. Rebuilding trust with users and search engines often requires significant resources, and the long-term financial implications can be substantial. Legal ramifications, such as fines or lawsuits, may also be incurred, increasing the overall cost of recovery.
Importance of Ongoing Security Measures, Link spam hacked website impact
The long-term impact of link spam underscores the critical need for proactive security measures. Ongoing vigilance and implementation of robust security protocols are essential to protect a website from future attacks. Regular security audits, vulnerability assessments, and proactive patching of security flaws are vital to maintain website integrity and protect against future compromises. The focus should not only be on immediate fixes but also on establishing a culture of security awareness and vigilance.
Table Summarizing Long-Term Impact Factors
| Type of Link Spam Attack | Impact on Reputation | Impact on Rankings | Recovery Costs |
|---|---|---|---|
| Comment Spam | Damage to website’s credibility, potentially leading to user distrust. | Significant drop in search engine rankings, difficulty in regaining visibility. | Moderate to high costs for cleaning up comments, updating content, and implementing security measures. |
| Hidden Links | Erosion of user trust, as users may not recognize manipulative practices. | Significant drop in search engine rankings, leading to a decrease in organic traffic. | High costs for detecting and removing hidden links, restoring search engine credibility. |
| Paid Links | Loss of credibility, users may perceive the website as manipulating search results. | Temporary or permanent penalties from search engines, impacting organic visibility. | High costs for removing paid links, repairing website structure, and re-establishing trust. |
| Forum Spam | Damage to website’s credibility, impacting user perception. | Significant drop in rankings due to search engine penalties for spamming forums. | Moderate to high costs for addressing forum posts, restoring website reputation, and upgrading security measures. |
Final Wrap-Up
In conclusion, link spam on hacked websites presents a multifaceted challenge. Understanding the different types of link spam, the tactics used to spread it, and the long-term effects is crucial. Implementing proactive security measures and utilizing effective detection and mitigation strategies are vital to protecting your website and reputation. The ongoing threat of link spam underscores the importance of consistent website security audits and a proactive approach to safeguarding online presence.