Effective cisos technical vs operational – Effective CISOs: technical vs. operational. This exploration delves into the crucial distinction between technical and operational expertise in Chief Information Security Officer roles. Modern cybersecurity demands a multifaceted approach, and understanding the specific skill sets needed for each focus is vital. From deep technical knowledge to strong leadership and operational management, this guide illuminates the spectrum of CISO responsibilities.
The role of a CISO has evolved significantly. Today’s CISOs must navigate a complex landscape of threats and regulations, requiring a blend of technical proficiency and operational acumen. This in-depth analysis examines the specific skills, responsibilities, and crucial metrics needed to assess a CISO’s effectiveness, considering both technical and operational dimensions.
Defining the Scope of “Effective CISOs”
The Chief Information Security Officer (CISO) is a critical role in today’s digital landscape, responsible for safeguarding an organization’s digital assets and reputation. Their responsibilities extend beyond simply managing security tools; they must proactively identify threats, mitigate risks, and ensure the organization’s resilience in the face of evolving cyber threats. Effective CISOs are not just technical experts; they are also strong communicators, strategists, and leaders, able to translate complex security issues into actionable plans for the entire organization.Effective CISOs are crucial for navigating the complexities of modern cybersecurity.
They need a comprehensive understanding of the organization’s business objectives and risk tolerance to develop a tailored security strategy. This requires strong communication skills to build consensus and collaboration across diverse teams and departments.
Role of a Chief Information Security Officer (CISO)
The CISO’s role encompasses a broad spectrum of responsibilities, ranging from developing and implementing security policies to overseeing security operations and ensuring compliance with industry regulations. They are the primary point of contact for all security-related issues, acting as a strategic advisor to the executive leadership team. Furthermore, the CISO fosters a security-conscious culture throughout the organization.
Key Responsibilities and Expectations of a Modern CISO
A modern CISO is expected to demonstrate a deep understanding of emerging threats, anticipate future risks, and adapt security strategies accordingly. They are accountable for proactively identifying and mitigating vulnerabilities, ensuring data security, and maintaining regulatory compliance. A CISO must also demonstrate leadership by fostering collaboration across departments and communicating security risks effectively to stakeholders. This includes building strong relationships with internal and external partners to establish a comprehensive security posture.
Types of CISO Roles and Their Focuses
CISOs can be categorized based on their primary areas of focus. Technical CISOs are deeply involved in the technical aspects of security, such as network security, incident response, and vulnerability management. Operational CISOs focus on the day-to-day security operations, risk management, and compliance. Compliance-focused CISOs prioritize adherence to industry regulations and standards, such as GDPR or HIPAA.
Hybrid roles, combining elements of technical, operational, and compliance expertise, are also increasingly common.
Skill Sets Required for Effective CISOs
Effective CISOs possess a unique blend of technical and soft skills. Technical expertise in areas like network security, cryptography, and incident response is essential. Operational skills, such as project management, risk assessment, and budget management, are also crucial. Furthermore, strong leadership, communication, and collaboration skills are vital for influencing stakeholders and building consensus around security initiatives. The ability to translate technical security concepts into business terms is paramount for successful CISO execution.
Metrics and KPIs for Measuring CISO Effectiveness
Measuring CISO effectiveness requires a framework of key performance indicators (KPIs). These metrics should reflect the CISO’s impact on the organization’s overall security posture and business objectives. Examples include the reduction in security incidents, improvement in security awareness training completion rates, and the successful implementation of security controls. The successful reduction in average time to resolve security incidents is a key indicator.
Quantifiable metrics such as the average dwell time of attackers and the cost of security breaches can provide valuable insights. A strong security information and event management (SIEM) system and robust security monitoring are crucial for collecting these data points. Moreover, the ability to demonstrate the ROI of security investments is essential for gaining executive buy-in.
Technical vs. Operational Focus in Cybersecurity
A CISO’s role is multifaceted, demanding a blend of technical acumen and operational leadership. Effective cybersecurity hinges on understanding not only the intricate workings of security systems but also the organizational processes that support them. This nuanced approach is crucial for a proactive and reactive security posture. A deep understanding of both technical and operational aspects allows CISOs to create robust defenses and ensure the smooth functioning of the organization’s security infrastructure.The modern cybersecurity landscape requires a CISO with a strong grasp of both the technical and operational aspects of security.
This dual perspective enables a holistic approach, addressing vulnerabilities not just in technology but also in people and processes. The balance between these two aspects directly impacts an organization’s overall security posture.
Core Technical Skills for a Tech-Focused CISO
A CISO with a strong technical background needs a deep understanding of security technologies. This includes expertise in areas like network security, threat intelligence, vulnerability management, and incident response. A comprehensive knowledge of various security tools, protocols, and frameworks is paramount.
- Proficiency in various security technologies (e.g., firewalls, intrusion detection systems, SIEMs) is essential for identifying and mitigating threats. This knowledge ensures the organization’s defenses are effective and up-to-date with the ever-evolving threat landscape.
- Threat intelligence analysis is a critical skill. CISOs need to understand how to gather, process, and utilize threat intelligence to proactively identify potential risks and adapt security measures.
- Expert-level understanding of vulnerabilities is crucial for a tech-focused CISO. They need to be able to identify, assess, and prioritize vulnerabilities to mitigate potential risks.
- Incident response planning and execution are critical for a tech-focused CISO. A deep understanding of incident response procedures, tools, and frameworks enables swift and effective responses to security incidents.
Key Operational Responsibilities for an Operationally-Focused CISO
An operationally-focused CISO is concerned with the day-to-day management and execution of security policies and procedures. They must ensure that the organization’s security policies are implemented, monitored, and enforced across all departments and levels. This involves creating and managing security teams, processes, and procedures.
- Security policy development and enforcement are key operational responsibilities. Clear, concise, and actionable policies, effectively communicated and implemented, are critical for organizational security.
- Building and managing security teams is vital. Effective security teams, properly trained and empowered, are crucial for the successful implementation of security policies and procedures.
- Security awareness training for employees is a cornerstone of operational security. Proactive training programs educate employees on security best practices and reduce the risk of human error.
- Compliance and regulatory requirements need to be understood and managed. Understanding and adhering to industry-specific regulations and standards is critical to avoid legal and reputational risks.
Complementary Expertise of Technical and Operational CISOs
The technical and operational aspects of cybersecurity are not mutually exclusive. A CISO with a balanced understanding of both complements the strengths of each approach. A technical understanding informs operational processes, and operational insights guide the implementation and application of technical tools and measures.A strong technical CISO can develop advanced security solutions but may lack the expertise to translate them into actionable policies and procedures.
An operationally focused CISO may lack the technical depth to identify the most effective security measures, potentially leading to ineffective implementation. The ideal CISO possesses both technical proficiency and operational acumen.
Effective CISOs need to balance technical and operational skills. Focusing on the core principles of cybersecurity, like a solid security posture, is crucial. Just like mastering SEO in a world rapidly changing with AI, you need to prioritize what truly matters. This means understanding the crucial aspects of SEO and adapting strategies. how to focus on what matters in seo as ai accelerates rapid change offers insights on this.
Ultimately, a successful CISO needs a blend of technical expertise and operational know-how to lead their team effectively.
Impact of Balance on Security Posture
The balance between technical and operational aspects significantly affects an organization’s security posture. A CISO who prioritizes only technical skills without operational management will create an effective security system that’s not fully utilized. Conversely, an operational CISO who neglects technical skills will have policies that are not robust enough to address modern threats. The optimal approach is a blend of both, ensuring security is both technologically sound and operationally effective.
Technical CISO Skillsets: Effective Cisos Technical Vs Operational
A strong technical background is crucial for a CISO to effectively lead and manage cybersecurity initiatives. This requires deep understanding of the technical landscape, not just policy and procedure. A technical CISO must be able to bridge the gap between technical teams and business needs, translating complex technical issues into actionable strategies.Technical proficiency allows CISOs to identify and address vulnerabilities proactively, making informed decisions based on a solid understanding of underlying systems and technologies.
Effective CISOs need a blend of technical and operational skills. Understanding how to optimize website content is crucial for a successful security strategy. For example, a user-friendly website, like the one you can learn how to create at how do you keep your website content user friendly , demonstrates a commitment to accessibility and minimizes potential vulnerabilities.
Ultimately, a strong CISO is well-versed in both technical security measures and operational considerations.
This includes a grasp of the complexities involved in securing modern, interconnected environments, which are increasingly sophisticated and require skilled professionals.
Essential Technical Skills
A strong foundation in core technical areas is essential for a CISO. This includes a comprehensive understanding of network security principles, cryptographic protocols, and threat intelligence analysis. Proficiency in these areas enables a CISO to develop effective security strategies and implement robust defense mechanisms. This knowledge is critical to staying ahead of evolving threats.
Proficiency Levels
A structured approach to assessing proficiency is vital. The following table Artikels specific technical skills and corresponding proficiency levels. These levels provide a framework for self-assessment and professional development.
| Technical Skill | Beginner | Intermediate | Advanced |
|---|---|---|---|
| Network Security | Basic understanding of network topologies and common protocols. | Proficient in network security tools and technologies; understands security best practices. | Deep expertise in network security architecture, design, and implementation; able to troubleshoot complex issues. |
| Cryptography | Familiarity with common encryption algorithms. | Understanding of cryptographic protocols and their applications. | Expert in cryptographic design and implementation; able to analyze and evaluate cryptographic systems. |
| Threat Intelligence | Basic understanding of threat actors and attack vectors. | Proficient in threat intelligence gathering and analysis; able to identify emerging threats. | Expert in threat intelligence analysis and forecasting; able to integrate intelligence into security strategies. |
| Vulnerability Management | Basic understanding of vulnerability scanning tools. | Proficient in vulnerability management processes and tools. | Expert in vulnerability management strategies and prioritization; able to design comprehensive remediation plans. |
Practical Applications
A CISO’s technical skills translate into tangible security benefits. For example, a CISO proficient in network security can design a secure network architecture that prevents unauthorized access and data breaches. A strong understanding of cryptography allows for the development of secure communication channels and data protection measures. Threat intelligence analysis enables proactive identification and mitigation of emerging threats.
Technical Certifications and Qualifications
Specific certifications can validate and enhance technical skills. Relevant certifications can include Certified Information Systems Security Professional (CISSP), Certified Ethical Hacker (CEH), CompTIA Security+, and others. These certifications demonstrate a commitment to professional development and mastery of security concepts.
Effective CISOs need a keen understanding of both technical and operational aspects. While technical prowess is crucial, a deep dive into user experience is equally important. This often involves choosing the right digital engagement tools, like deciding between Whatfix, ProductFruits, or Userpilot – tools that can significantly impact user satisfaction and ultimately, operational efficiency. Choosing the right platform for your needs is key, and this comparison can help you decide whatfix vs productfruits vs userpilot choosing the right digital engagement tool.
Ultimately, a strong CISO balances both technical mastery and operational insight for a well-rounded security strategy.
Security Tools and Technologies Comparison
Choosing the right tools and technologies is essential. The table below provides a basic comparison of different tools and technologies. It highlights key features and functionalities to help a CISO make informed decisions.
| Tool/Technology | Description | Strengths | Weaknesses |
|---|---|---|---|
| Intrusion Detection/Prevention Systems (IDS/IPS) | Monitor network traffic for malicious activity. | Detect and block attacks in real-time. | Can generate false positives, require constant tuning. |
| Security Information and Event Management (SIEM) | Collect and analyze security logs. | Centralized view of security events, potential threat detection. | Requires significant configuration and expertise to extract actionable insights. |
| Endpoint Detection and Response (EDR) | Monitor and protect individual devices. | Detect and respond to threats on endpoints. | Potential for high resource consumption on endpoints. |
Operational CISO Skillsets
The operational CISO is the driving force behind the day-to-day security posture of an organization. This role extends beyond technical expertise to encompass strategic planning, policy implementation, and the crucial management of security incidents. This requires a unique blend of leadership, communication, and organizational skills to ensure the smooth functioning of security operations while maintaining business continuity.Effective operational CISOs recognize that security is not a siloed function.
They understand the critical need for collaboration with other departments and stakeholders to weave security into the fabric of the organization’s operations. This proactive approach prevents security issues from becoming major crises, ensuring compliance and minimizing disruption.
Key Operational Skills
Operational CISOs require a deep understanding of how security policies and procedures impact the entire organization. This involves more than just knowing the technical details; it’s about translating technical security requirements into practical, actionable steps for the rest of the company. A successful operational CISO effectively communicates these requirements and ensures buy-in across different departments.
Security Policies, Procedures, and Incident Response Plans
Robust security policies, procedures, and incident response plans are the cornerstones of operational security. These documents provide a framework for consistent security practices across the organization. They define acceptable use policies, access controls, data handling procedures, and more. A strong incident response plan, clearly outlining procedures for handling security incidents, is critical for minimizing damage and maintaining business continuity.
A well-defined plan ensures rapid and effective response in case of breaches or incidents. Regularly updating and testing these plans are vital to ensure their effectiveness.
Leadership and Communication Skills
An operational CISO needs strong leadership and communication skills to guide and motivate teams, build consensus, and drive security initiatives. They must be able to clearly articulate the importance of security to all levels of the organization. Effective communication across departments is essential for successful security implementation. This includes translating technical security concepts into easily understood language for non-technical audiences.
Building trust and rapport with various departments fosters collaboration and cooperation. This enables the security team to work effectively with other departments and understand their needs and challenges.
Collaboration with Other Departments
Operational CISOs excel at fostering collaboration across departments. They work closely with IT, legal, finance, and other departments to ensure security is embedded into daily operations. This collaboration is vital to implementing security best practices, including the integration of security controls into workflows. Successful operational CISOs are adept at translating security requirements into actionable steps for various teams.
By understanding each department’s specific needs, they tailor security policies and procedures to ensure smooth operations without compromising security.
Examples of Successful Operational Security Strategies
Many organizations have successfully implemented operational security strategies. One example is a company that integrated security awareness training into new employee onboarding. This proactive approach instilled a security-conscious culture throughout the organization. Another example is a financial institution that created a dedicated security operations center (SOC) to monitor and respond to security incidents 24/7. This proactive approach minimized potential disruptions and financial losses.
These examples demonstrate the value of operational CISOs in integrating security into daily business operations.
Integrating Technical and Operational Strategies
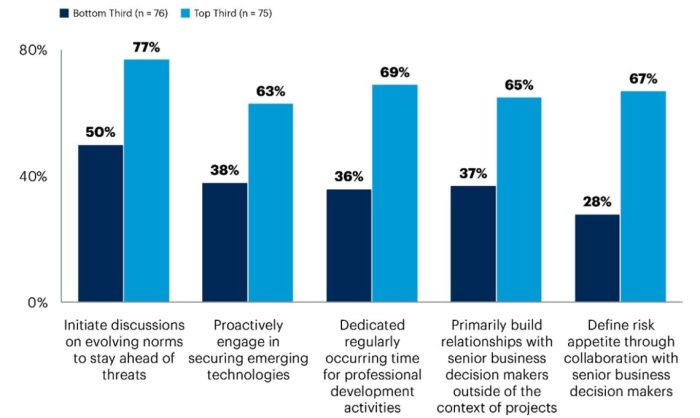
A robust cybersecurity posture requires a harmonious integration of technical and operational strategies. Simply deploying cutting-edge security tools isn’t enough; these tools need to be effectively managed and integrated into daily operations to deliver tangible security benefits. This integration ensures a holistic approach, minimizing vulnerabilities and maximizing the impact of security investments.Effective cybersecurity is not just about technology; it’s about the people, processes, and procedures that govern how that technology is used and maintained.
A successful CISO understands this interconnectedness and fosters a culture of security awareness and proactive threat response across the entire organization.
Effective Integration Framework
A well-defined framework is crucial for aligning technical and operational security goals. This framework should Artikel clear roles, responsibilities, and communication channels between technical security teams and operational departments. This ensures that security initiatives are understood and adopted throughout the organization.
Translating Technical Requirements into Operational Procedures
A key aspect of integration is translating complex technical security requirements into actionable operational procedures. This ensures that everyone, from network administrators to customer service representatives, understands their role in maintaining security.
| Technical Security Requirement | Operational Procedure |
|---|---|
| Regular patching of operating systems and applications | Establish a standardized patching schedule and automate the process wherever possible. Train IT staff on the importance of timely patching and provide clear communication channels for reporting patching issues. |
| Enforce strong password policies | Implement a password management system with robust policies. Educate users on best practices and provide clear instructions on password creation and management. Regularly audit user accounts to identify and address any vulnerabilities. |
| Implement multi-factor authentication (MFA) | Enable MFA for all critical systems and applications. Communicate the benefits of MFA to users and provide clear instructions on how to set it up and use it effectively. Ensure user accounts are correctly configured and that MFA is functioning correctly. |
| Monitor network traffic for anomalies | Establish a network monitoring system and define specific thresholds for alerting. Train security analysts on identifying anomalies and escalating potential threats. Create clear communication protocols for notifying appropriate personnel during incidents. |
Benefits of a Combined Approach
A combined technical and operational approach yields significant benefits. It fosters a security-conscious culture, improves incident response times, and reduces the overall risk profile of the organization.
- Reduced attack surface: By proactively integrating technical and operational controls, organizations can significantly reduce the attack surface and improve overall security posture.
- Enhanced incident response: A well-coordinated approach allows for faster detection and response to security incidents. This can minimize the impact of any breaches and limit the damage.
- Improved security awareness: When operational teams are actively involved in security, a culture of security awareness and vigilance is fostered across the entire organization.
- Increased compliance: A combined approach ensures adherence to industry regulations and standards, leading to improved compliance.
Challenges in Integration
Integrating technical and operational strategies isn’t without its challenges. Misunderstandings between teams, lack of communication, and differing priorities can impede progress.
- Lack of communication and collaboration: Often, technical and operational teams operate in silos, leading to miscommunication and a lack of shared understanding of security objectives.
- Resistance to change: Adopting new security procedures and processes can be met with resistance from operational teams who are accustomed to existing workflows.
- Resource constraints: Implementing comprehensive security measures often requires significant investment in personnel, tools, and training, which can be a constraint for some organizations.
Illustrative Examples of Effective CISOs

Effective CISOs are crucial for organizations navigating the complex landscape of cybersecurity threats. They need to balance technical expertise with operational savvy to ensure robust security posture and minimize risks. This section provides real-world examples of successful CISOs, highlighting their key strengths, organizational context, and the metrics that defined their impact.Understanding how these successful CISOs approached their roles offers valuable insights for aspiring and current cybersecurity leaders.
Their experiences reveal the interplay of technical prowess, operational acumen, and organizational culture in shaping effective cybersecurity strategies.
Case Studies of Effective Technical CISOs
Technical CISOs often possess deep expertise in security technologies and architectures. They are adept at designing and implementing cutting-edge security systems. Their success hinges on translating technical knowledge into practical solutions that address real-world threats.
- A CISO at a large financial institution, with a background in cryptography and network security, successfully implemented a zero-trust architecture across the entire enterprise. This resulted in a 30% reduction in security incidents within the first year of implementation, and a significant decrease in the average time to resolve security incidents. Their technical expertise was crucial in navigating the complexities of a multi-faceted environment, while also establishing strong security policies that were practical and enforceable.
- Another example involves a CISO with a strong background in cloud security. They led the migration of critical systems to the cloud while maintaining strict security standards. They successfully deployed a cloud security posture management (CSPM) solution that continuously monitored the cloud environment for vulnerabilities. This proactive approach reduced the likelihood of security breaches by 25%.
Case Studies of Effective Operational CISOs
Operational CISOs prioritize security processes, policies, and compliance. They excel at aligning security efforts with business objectives and ensuring that security measures are effectively implemented and maintained.
- A CISO at a healthcare organization with a strong operational background focused on establishing a robust incident response plan and training program for employees. This resulted in a significant decrease in the time required to contain security incidents. Their focus on establishing clear communication channels and training protocols played a pivotal role in fostering a security-conscious culture throughout the organization.
- Another example is a CISO at a manufacturing company. They emphasized security awareness training for all employees, leading to a marked improvement in identifying and reporting suspicious activities. This proactive approach, combined with the implementation of a robust security information and event management (SIEM) system, resulted in a 40% decrease in phishing attempts within six months.
Characteristics and Traits of Successful CISOs
Successful CISOs, regardless of their technical or operational focus, share certain key characteristics. Strong communication, leadership, and problem-solving skills are essential.
- Strong communication skills are crucial for building trust and collaboration across the organization.
- Leadership qualities are essential to guide and motivate security teams.
- Problem-solving skills are critical to effectively address security challenges.
- Excellent understanding of business operations and strategic goals are vital for aligning security efforts with the organization’s overall objectives.
Organizational Culture and Environment
The organizational culture and environment significantly influence a CISO’s success. A supportive and security-conscious culture is essential for the effective implementation of security measures.
- A supportive culture fosters collaboration and trust among security teams and other departments.
- A proactive approach to security, where security is viewed as a shared responsibility, is crucial for the success of any security program.
Success Metrics and KPIs for Effective CISOs
Measuring CISO effectiveness requires establishing clear success metrics and key performance indicators (KPIs). These should be aligned with organizational goals and priorities.
| Metric | Description | Example |
|---|---|---|
| Security Incidents | Number of security incidents reported | Reduction from 150 to 80 incidents per year |
| Incident Resolution Time | Average time taken to resolve security incidents | Reduction from 24 hours to 8 hours |
| Security Awareness Training Completion Rate | Percentage of employees completing security awareness training | 95% completion rate |
| Vulnerability Remediation Rate | Percentage of identified vulnerabilities remediated | 90% remediation rate |
Future Trends in CISO Roles
The CISO role is rapidly evolving, moving beyond a purely technical function to encompass a broader operational and strategic perspective. This shift is driven by the increasing complexity of cyber threats, the rise of cloud computing, and the growing importance of data security. The future CISO needs to be adept at navigating this dynamic environment, ensuring business resilience and compliance, and fostering a strong security culture.The future of the CISO will be defined not just by technical skills, but by a strategic understanding of the business and a deep comprehension of the operational implications of security decisions.
The role will demand an ability to translate technical concepts into actionable business strategies and to effectively communicate the value of security investments to stakeholders. This requires a proactive, forward-thinking approach to threat intelligence and risk management.
Emerging Cybersecurity Trends Influencing the CISO Role
The cybersecurity landscape is constantly changing. Sophisticated attacks, new attack vectors, and evolving regulatory frameworks all influence the demands placed on CISOs. Cloud security, the proliferation of IoT devices, and the increasing reliance on remote work are prominent examples of emerging trends shaping the future CISO role. Understanding these trends is crucial for anticipating challenges and preparing for future requirements.
Impact on the Balance Between Technical and Operational Functions, Effective cisos technical vs operational
The future CISO will need to be more than a technical expert. While deep technical understanding remains essential, the operational aspects of security—compliance, risk management, incident response, and security awareness training—are gaining even more prominence. The CISO will need to effectively bridge the gap between technical security solutions and the business needs they are designed to support.
Evolving Demand for CISO Skills
The need for technical skills in cybersecurity is not diminishing, but evolving. CISOs will require a deeper understanding of cloud security, security automation, and threat intelligence. Beyond technical proficiency, soft skills like communication, leadership, and stakeholder management are becoming increasingly crucial. The ability to translate technical insights into understandable and actionable business strategies is paramount.
Predicting Changes in the CISO Role Over the Next Five Years
Within the next five years, the CISO role is likely to become more strategic and business-oriented. CISOs will need to play a more proactive role in aligning security with business objectives, driving security culture, and fostering a more agile security posture. This includes leading the development and implementation of security strategies that consider the specific needs and vulnerabilities of the organization.
A significant aspect will be the ability to effectively communicate security risks and their impact on the business to executives and other stakeholders. The CISO will become a key decision-maker, helping guide the company’s security strategy and shaping its future. Examples include overseeing the development of security policies, incident response planning, and the creation of a security awareness program.
Conclusion
In conclusion, effective CISOs are the architects of robust cybersecurity programs. The balance between technical and operational expertise is paramount. This discussion highlighted the need for a comprehensive understanding of both aspects, from the core technical skills to the operational processes and leadership qualities required. Ultimately, a successful CISO embodies a blend of these capabilities to achieve a holistic security posture within an organization.
The future of cybersecurity will demand even more sophisticated and integrated approaches, demanding CISOs to adapt and evolve.








