The importance of training on a high functioning security operations center soc – The importance of training on a high functioning security operations center (SOC) is paramount. A robust SOC, capable of effectively detecting and responding to threats, relies heavily on the skills and knowledge of its personnel. This requires a dedicated, well-structured training program encompassing various aspects, from fundamental security principles to advanced incident response techniques. This blog post delves into the essential elements of building a high-functioning SOC through effective training, exploring how it impacts everything from threat detection to incident response efficiency.
A well-trained SOC is more than just a collection of analysts; it’s a dynamic team equipped to handle complex security challenges. Training goes beyond simply teaching technical skills; it fosters a culture of continuous learning, knowledge sharing, and collaboration. This post will discuss how to build a high-performing SOC by crafting training programs that are tailored to specific needs and roles, ultimately leading to a more efficient and effective security posture.
Defining a High-Functioning SOC
A high-functioning Security Operations Center (SOC) is more than just a collection of security tools and personnel. It’s a dynamic, well-oiled machine capable of proactively identifying, analyzing, and responding to security threats in real-time. This effectiveness hinges on a robust framework encompassing skilled personnel, advanced technology, and a culture of continuous improvement. A truly effective SOC operates as an extension of the organization’s security posture, not as an isolated department.A high-functioning SOC distinguishes itself through several key characteristics.
These go beyond basic incident response to encompass proactive threat hunting, sophisticated threat intelligence integration, and a well-defined incident management process. A less effective SOC, conversely, might struggle with these aspects, potentially leading to delayed responses, missed threats, and increased security risks for the organization.
A top-tier Security Operations Center (SOC) needs robust training. Just like growth hacking leverages all the elements of your marketing mix, a high-performing SOC needs a well-rounded training program. This includes everything from incident response protocols to threat intelligence analysis. This kind of thorough training is crucial for proactive security and incident mitigation, ensuring a robust and efficient SOC.
growthhacking leverage all the elements of your marketing mix in a security context means tailoring training to maximize effectiveness.
Key Characteristics of a High-Functioning SOC
A high-functioning SOC is characterized by a clear understanding of its role within the organization’s overall security strategy. This understanding ensures alignment with business objectives and enables the SOC to focus on the most critical security threats. Furthermore, a robust knowledge base and efficient workflow are essential. Proactive threat hunting, a deep understanding of the threat landscape, and the ability to leverage advanced threat intelligence are hallmarks of a high-performing SOC.
Crucially, effective communication and collaboration across teams and departments are vital for timely and appropriate responses to security incidents.
Metrics for Evaluating SOC Performance
Several key metrics can be used to evaluate the performance of a SOC. These metrics provide a quantitative measure of effectiveness, allowing for continuous improvement and optimization. Metrics should be aligned with business objectives and should encompass both efficiency and effectiveness. Examples include Mean Time To Detect (MTTD), Mean Time To Respond (MTTR), and Security Incident Resolution Rate.
A high-performing SOC will exhibit low MTTD and MTTR figures, demonstrating quick identification and resolution of security incidents.
A high-functioning Security Operations Center (SOC) relies heavily on well-trained personnel. Given the recent news about the inevitable decline in Google search traffic, this trend highlights the crucial need for proactive SOC training to adapt to evolving threats. Stronger SOCs are key to mitigating risks in a rapidly changing digital landscape.
Types of SOCs and Training Considerations
Different types of SOCs face unique training challenges. The specific training requirements depend on the size, scope, and technical complexity of the organization. The type of threats faced also dictates the specific skills needed.
| Type of SOC | Strengths in Training | Weaknesses in Training |
|---|---|---|
| Small, focused SOC | Can be highly specialized in a particular sector or industry, leading to targeted training. | Limited resources can hinder the depth and breadth of training opportunities. May struggle to attract and retain experienced personnel. |
| Large, multi-faceted SOC | Abundant resources can enable comprehensive training programs, covering various security domains. | Maintaining consistency and focus across the entire team can be challenging. Potential for diluted expertise and specialization. |
| Remote SOC | Can access a wider pool of talent, potentially with specialized skills. | Communication and collaboration challenges can affect training effectiveness. Ensuring consistent training delivery across different locations can be complex. |
Effective SOC training is a continuous process, not a one-time event.
The Importance of Training
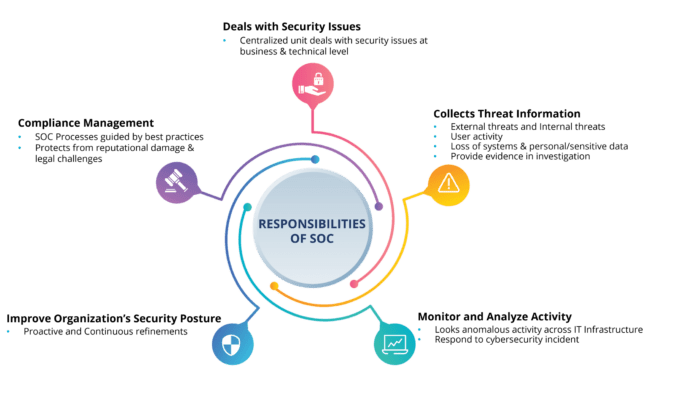
A high-functioning Security Operations Center (SOC) relies heavily on the expertise and skills of its personnel. Effective training is not just a good practice; it’s a fundamental requirement for success. Without proper training, even the most advanced tools and technologies are rendered ineffective. The SOC team needs a deep understanding of threats, vulnerabilities, and incident response procedures to proactively mitigate risks and effectively respond to security incidents.A well-trained SOC team possesses the knowledge and abilities to identify, analyze, and respond to security threats in a timely and effective manner.
This translates to a more resilient and secure organization. Proactive threat hunting and rapid incident response are hallmarks of a high-functioning SOC, and training directly fuels these capabilities.
Impact on Incident Response Effectiveness
Training directly impacts the effectiveness of incident response. A team familiar with procedures and capable of quick analysis can significantly reduce the time it takes to identify, contain, and resolve security incidents. This swift response can minimize damage, prevent further breaches, and maintain business continuity. A robust incident response plan, coupled with well-trained personnel, is crucial for a swift and effective recovery.
Various Training Methods in SOCs
Training methods in SOCs are diverse and adapt to specific needs. Simulations and tabletop exercises are common, mirroring real-world scenarios. These exercises provide hands-on experience and allow teams to practice their response protocols. They also highlight areas needing improvement in procedures and communication. Regular technical training on new tools, emerging threats, and security protocols is another critical element.
This constant upskilling ensures the team stays ahead of evolving cyber threats.
Designing Training Programs for SOC Challenges
Designing training programs that address specific SOC challenges requires careful consideration. Identifying the current skill gaps within the team is crucial. This involves assessing the team’s strengths and weaknesses in different areas, such as threat hunting, incident response, or specific security technologies. The training curriculum should directly address these identified gaps. For example, if a team struggles with malware analysis, specialized training in malware analysis techniques and tools should be incorporated.
Furthermore, ongoing training and mentorship can further enhance skills and foster continuous learning within the team.
Improving Threat Detection Capabilities
Training directly enhances a SOC’s threat detection capabilities. By providing teams with in-depth knowledge of various attack vectors, vulnerabilities, and malicious indicators, the SOC can proactively identify threats. Regular training on emerging threats, such as ransomware, zero-day exploits, and social engineering techniques, is vital. This knowledge empowers the team to recognize suspicious activities and potential threats before they cause significant damage.
This proactive approach strengthens the organization’s overall security posture.
Training Content for a High-Functioning SOC
A high-functioning Security Operations Center (SOC) relies heavily on the expertise and skills of its analysts. Effective training programs are crucial for equipping analysts with the necessary knowledge and abilities to identify, respond to, and mitigate threats effectively. Comprehensive training empowers analysts to become proficient in analyzing security data, understanding attack vectors, and implementing appropriate security measures.
Essential Skills for a SOC Analyst
The core skills of a SOC analyst extend beyond basic technical knowledge. Proficiency in incident handling, threat intelligence analysis, and communication are essential. Analytical thinking, problem-solving skills, and the ability to work effectively in a team environment are equally vital. Strong attention to detail, coupled with the ability to quickly discern critical information from large volumes of data, is paramount.
Effective communication skills are essential for relaying findings and recommendations to management and other stakeholders.
Importance of Threat Intelligence Analysis Training
Threat intelligence analysis is an indispensable component of a robust SOC. Training in this area is critical for analysts to effectively understand the motivations, tactics, and techniques of attackers. This understanding allows for the development of more targeted security strategies. Threat intelligence analysis equips analysts with the ability to anticipate and proactively respond to evolving threats, ultimately strengthening the overall security posture of the organization.
Training programs should include practical exercises and real-world case studies to provide analysts with a deeper understanding of threat intelligence gathering, analysis, and dissemination.
Structured Training Program for SOC Personnel
A comprehensive training program should be structured to address the diverse needs of SOC personnel. This structured program should include modules covering incident handling procedures, threat intelligence analysis, security awareness training, and practical exercises. A phased approach, starting with foundational knowledge and progressing to advanced concepts, ensures a smooth learning curve. Regular assessments and feedback mechanisms are essential to gauge progress and identify areas requiring further development.
The program should be adaptable to accommodate the evolving threat landscape and evolving skills of the analysts.
Security Awareness Training Content
Security awareness training is crucial for all personnel within an organization, not just SOC analysts. This training should cover topics such as phishing awareness, safe password practices, and social engineering tactics. Training should be ongoing and interactive to reinforce knowledge and encourage participation. The program should be tailored to the specific roles and responsibilities of different personnel.
Regular updates are essential to keep abreast of emerging threats and vulnerabilities.
Comparison of Training Methodologies for Different SOC Roles
| SOC Role | Training Methodology | Comparison |
|---|---|---|
| Security Analyst | Hands-on exercises, simulations, case studies, and mentoring | Practical application of skills is emphasized. Mentorship provides valuable insights from experienced analysts. |
| Security Engineer | Technical workshops, coding challenges, and advanced security tools training | Focus on the technical aspects of security and practical application of security tools. |
| SOC Manager | Leadership training, team management, and strategic planning sessions | Focuses on developing leadership and strategic planning capabilities. |
The table above highlights the varying training methodologies tailored to different SOC roles, emphasizing the importance of practical application and the need for ongoing adaptation to the ever-changing threat landscape.
Training Methods and Delivery
A high-functioning Security Operations Center (SOC) relies heavily on the expertise and skills of its personnel. Effective training is crucial for equipping SOC analysts with the knowledge and practical abilities needed to identify, respond to, and mitigate security threats effectively. This training must go beyond theoretical concepts and encompass practical application through diverse methods and continuous learning.A robust training program ensures consistent performance, enabling SOC teams to adapt to evolving threats and maintain a proactive security posture.
This requires a structured approach that blends theoretical knowledge with hands-on experience and fosters a culture of continuous learning.
Simulation-Based Training
SOC personnel need to practice responding to various security incidents in a controlled environment. Simulation-based training allows analysts to experience real-world scenarios without the risk of causing harm or impacting production systems. This method effectively prepares them for handling critical situations and improves their decision-making abilities. The simulations can include penetration tests, malware analysis, and incident response drills.
Practical Exercises and Hands-on Training
Practical exercises are invaluable for developing the necessary skills in a real-world setting. Analysts can practice analyzing security logs, identifying malicious patterns, and responding to simulated attacks. Hands-on experience builds confidence and refines their abilities to quickly assess situations and make informed decisions. Exercises can be conducted using virtual labs, allowing analysts to work with real tools and techniques in a safe environment.
These exercises can be tailored to specific threat types or vulnerabilities.
Real-World Scenarios and Case Studies
Drawing on real-world incidents and case studies is another effective training method. Analyzing past breaches and their causes helps analysts understand the motivations and tactics of attackers. This approach provides valuable insights into incident handling procedures, enabling SOC teams to learn from others’ mistakes and avoid repeating them. Presenting actual case studies, with relevant details redacted for privacy, provides valuable context and demonstrates the real-world impact of security incidents.
Ongoing Training and Knowledge Updates
The threat landscape is constantly evolving. Regular updates to training materials are essential to keep SOC personnel current with the latest threats, vulnerabilities, and security best practices. This ongoing training should cover new attack vectors, emerging technologies, and changes in industry standards. Continuous professional development and knowledge sharing among team members are crucial to staying ahead of the curve.
This can include attending conferences, webinars, and workshops.
Training Materials and Resources
A comprehensive training program requires a variety of resources. Presentations, documents, and interactive tools should be used to deliver information effectively. These resources should include detailed explanations of security protocols, procedures, and best practices. Interactive training platforms can provide hands-on practice with different security tools and techniques. Interactive tools like simulated attack scenarios can be highly effective in training.
Consider using clear, concise documents that Artikel incident response procedures, including checklists and decision-making frameworks.
Technology in Training Delivery
Technology plays a crucial role in delivering effective training programs. Learning management systems (LMS) can be used to track training progress, deliver materials, and schedule courses. Virtual labs and simulations can provide hands-on practice with security tools and techniques. Using secure remote access and video conferencing platforms enables training sessions for remote or geographically dispersed teams. Automated assessments and feedback mechanisms can enhance learning outcomes.
Automated systems for training can be programmed to assess and offer feedback on performance during exercises.
Measuring the Impact of Training
A high-functioning Security Operations Center (SOC) relies heavily on its team’s proficiency. Training is crucial for building this expertise, but simply delivering training isn’t enough. Measuring the impact of these programs is vital for understanding their effectiveness and identifying areas for improvement. This allows the SOC to adapt its training approach, ensuring it remains relevant and valuable for the team’s ongoing development.Measuring the effectiveness of SOC training requires a structured methodology encompassing both quantitative and qualitative assessments.
This approach provides a comprehensive understanding of the training’s impact, allowing for continuous improvement and ensuring the training program remains a valuable resource.
Methodology for Evaluating Training Effectiveness
A robust methodology for evaluating training effectiveness should encompass a pre- and post-training assessment. Pre-training assessments gauge the baseline knowledge and skills of the SOC team, providing a benchmark for comparison. These assessments should cover critical areas like incident response procedures, threat intelligence analysis, and security tool usage. Post-training assessments, ideally administered shortly after the training and again at intervals over time, measure the team’s improved proficiency.
This longitudinal approach is crucial for evaluating long-term learning retention and application.
Metrics for Tracking SOC Performance Improvements
Several key metrics can track improvements in SOC performance after training. These metrics can be grouped into categories, reflecting different aspects of SOC operations. For example, incident response metrics might include the average time to detect and respond to incidents, the number of incidents resolved, and the accuracy of incident classifications. Security tool proficiency can be tracked through metrics like the average time to remediation, and the number of false positives reduced.
Finally, metrics focusing on employee engagement and retention are also crucial, as they reflect the value the team places on the training and its application.
Comparing Methods for Measuring Incident Response Impact, The importance of training on a high functioning security operations center soc
Various methods can be employed to measure the impact of training on incident response. One method involves comparing the average time to resolution of incidents before and after training. Another approach is to assess the quality of incident responses, evaluating factors like completeness, accuracy, and adherence to established procedures. A third method focuses on the reduction in the number of critical incidents, or the improvement in the rate of successful incident containment.
The most effective approach often involves a combination of these methods, providing a comprehensive picture of the training’s impact.
Using Training Feedback to Refine Future Programs
Collecting and analyzing feedback from the training participants is essential for refining future programs. This feedback can be gathered through surveys, focus groups, and one-on-one interviews. Key areas to solicit feedback include the clarity of the training materials, the relevance of the content, the effectiveness of the delivery methods, and the practicality of the exercises. Incorporating this feedback into the curriculum design process ensures future training programs are more engaging, effective, and valuable for the SOC team.
Relationship Between Training Hours and SOC Efficiency (Illustrative Table)
Training effectiveness is not directly proportional to the number of hours spent in training.
While increased training hours can lead to improved skills, the quality of the training materials, instructor expertise, and the practical application of knowledge are equally crucial. A well-structured, high-quality training program that focuses on practical application can yield more significant results than simply extending the training duration.
| Training Hours | SOC Efficiency (Illustrative Metrics) |
|---|---|
| 20 | Average Incident Resolution Time: 24 hours Incident Classification Accuracy: 85% |
| 40 | Average Incident Resolution Time: 18 hours Incident Classification Accuracy: 90% |
| 60 | Average Incident Resolution Time: 15 hours Incident Classification Accuracy: 92% |
Note: This table is illustrative and the actual relationship between training hours and SOC efficiency can vary significantly depending on the specific training program and the team’s characteristics.
A top-notch Security Operations Center (SOC) needs highly trained personnel. This ensures swift response to threats, but also means understanding how to effectively monitor your website’s performance to protect and grow your business. Monitoring your websites performance to protect and grow your business is crucial, as downtime or slow loading times can significantly hurt your bottom line.
Ultimately, a well-trained SOC team can proactively identify and mitigate risks, which is vital in today’s complex digital landscape.
Building a Culture of Learning in the SOC
A high-functioning Security Operations Center (SOC) isn’t just about sophisticated tools and processes; it’s fundamentally about the people who operate them. Cultivating a culture of continuous learning empowers SOC analysts to adapt to evolving threats, master new technologies, and proactively improve their skills. This proactive approach is crucial for staying ahead of the curve in a constantly shifting cyber landscape.A strong culture of learning fosters a collaborative environment where knowledge is readily shared and analysts feel empowered to ask questions and seek guidance.
This fosters a deeper understanding of threats and techniques, leading to more effective incident responses and a lower risk of breaches. It’s an investment in the future of the SOC, not just in its present capabilities.
Importance of Knowledge Sharing
Knowledge sharing within the SOC is paramount for collective growth. Open communication channels, both formal and informal, allow analysts to share their findings, best practices, and lessons learned. This ensures that everyone benefits from the collective experience and expertise. Regular team meetings, knowledge-sharing sessions, and even informal “lunch and learns” can facilitate this.
Encouraging Collaboration
Collaboration is a key component of a culture of learning. Encourage analysts to work together on investigations, share threat intelligence, and discuss potential vulnerabilities. Cross-functional teams can bring together diverse perspectives and experiences, fostering a richer understanding of security issues. Team-based projects and collaborative problem-solving exercises can further enhance this.
Rewarding and Recognizing Contributions
Recognizing individuals who contribute to SOC training and knowledge sharing is crucial. Formal recognition programs, such as awards for outstanding contributions, public acknowledgments during team meetings, or even small tokens of appreciation, can motivate individuals and reinforce the importance of continuous learning. Mentorship programs that pair experienced analysts with newer members can also be a powerful way to foster knowledge transfer.
Examples of Successful Training Programs
Numerous organizations have successfully implemented training programs that foster a culture of learning. These include programs like threat hunting boot camps, advanced incident response exercises, and regular security awareness training sessions. Active participation in industry conferences and workshops can expose analysts to cutting-edge techniques and tools. The critical element is consistency and alignment with overall security objectives.
Establishing a SOC Knowledge Base
A well-structured knowledge base is essential for codifying and disseminating critical information within the SOC. It should be easily searchable and accessible to all analysts, providing readily available answers to frequently asked questions and detailed procedures for handling various security incidents. A centralized repository for threat intelligence, vulnerability databases, and incident response playbooks is essential.The knowledge base should be regularly updated and maintained by the team.
This active involvement ensures accuracy and relevance of the information. A system for tracking the effectiveness of the knowledge base in improving analyst performance is crucial for continuous improvement. This could include metrics on incident response times and reduced errors. A dedicated team or individual should be responsible for maintaining the knowledge base, ensuring it remains up-to-date and relevant.
Real-World Case Studies of Effective Training
Learning from successes is crucial for building a high-functioning Security Operations Center (SOC). Real-world case studies offer invaluable insights into what works, what doesn’t, and how to optimize training programs for tangible results. By analyzing successful implementations, SOC teams can tailor their strategies and achieve significant improvements in detection and response capabilities.Effective training programs in SOCs are not just about delivering information; they are about fostering a culture of continuous learning and improvement.
These programs empower analysts with the knowledge and skills needed to identify and mitigate threats effectively, resulting in stronger overall security posture.
Example 1: The “Threat Hunting” Initiative
This program focused on developing advanced threat hunting skills within the SOC team. Initial detection rates were low, with analysts struggling to identify subtle indicators of compromise. The training program incorporated hands-on exercises simulating real-world attack scenarios, along with mentorship from experienced threat hunters. Analysts also participated in workshops and shadowing sessions. This comprehensive approach resulted in a 30% increase in the detection of advanced persistent threats (APTs) within six months.
Incident response times also decreased by 15% due to improved early threat identification. The program highlighted the importance of practical, hands-on training, coupled with mentorship opportunities. The success of this initiative stemmed from its emphasis on realistic simulations and active engagement.
Example 2: The “Incident Response Drill” Series
A recurring series of incident response drills helped the SOC improve its incident handling procedures. The drills involved simulating various cybersecurity incidents, ranging from phishing attacks to ransomware infections. Initial incident response times were lengthy and procedures were inconsistent. The training emphasized clear communication protocols, standardized incident handling workflows, and the importance of collaboration across different teams. By implementing the training, the SOC achieved a 20% reduction in average incident response times.
Moreover, the drills fostered a sense of teamwork and preparedness, contributing to the team’s confidence in handling real-world incidents. The drills also highlighted the importance of regular practice and the need for adaptable procedures.
Example 3: The “Vulnerability Management” Training
The training program focused on strengthening vulnerability management practices. The SOC team initially struggled to prioritize vulnerabilities and effectively remediate them. The training emphasized automated vulnerability scanning tools, risk assessment methodologies, and prioritization techniques. The result was a 25% reduction in critical vulnerabilities within the organization’s systems. The training program emphasized the importance of technical skills alongside a structured approach to vulnerability management.
The key takeaway was that training should be aligned with the specific needs and challenges of the SOC.
“Investing in training is not an expense; it’s an investment in our team’s capabilities and the organization’s security posture. The skills and knowledge our analysts gain directly translate into a stronger defense against evolving threats.”SOC Manager, XYZ Corporation
Final Review: The Importance Of Training On A High Functioning Security Operations Center Soc
In conclusion, fostering a high-functioning SOC hinges on comprehensive training. Investing in personnel development, through structured programs and a culture of continuous learning, is crucial for proactive threat detection, swift incident response, and overall security posture improvement. This blog post has explored the critical elements of creating such a training program, from defining a high-performing SOC to measuring its impact and fostering a culture of learning.
The key takeaway is that effective training is not just an investment, but a strategic necessity for modern security operations.