Endpoint security s biggest issue claiming compliance out of the box – Endpoint security’s biggest issue is claiming compliance “out of the box.” This often masks critical vulnerabilities and misconfigurations, leading to serious risks for organizations. From inadequate patching to configuration drift, the gap between advertised compliance and actual security posture can be significant. This exploration dives deep into the problems with these out-of-box claims, examining the potential consequences and outlining best practices for genuine compliance.
The discussion will begin by defining what “compliance out of the box” truly means in the context of endpoint security, including relevant compliance standards like HIPAA, GDPR, and PCI DSS. We’ll then analyze common issues with these claims, such as security gaps and the impact of inadequate patching. Furthermore, we’ll explore the severe consequences of false compliance claims, from reputational damage to hefty financial penalties and data breaches.
Finally, we’ll provide a structured method for evaluating endpoint security solutions, best practices for achieving true compliance, and case studies of past failures.
Defining “Compliance Out of the Box” in Endpoint Security
The promise of “compliance out of the box” in endpoint security often sounds appealing, suggesting effortless adherence to industry regulations. However, this marketing buzzword requires careful scrutiny. It implies that an endpoint security solution, simply by being installed, automatically meets all necessary compliance standards. The reality is far more nuanced.This promise masks the significant effort required to achieve and maintain true compliance, often requiring substantial configuration, ongoing updates, and careful auditing.
Understanding the intricacies of “compliance out of the box” is crucial for organizations seeking to protect their data and avoid costly penalties.
Defining Compliance Out of the Box
“Compliance out of the box” in endpoint security implies that a security solution, upon initial installation and minimal configuration, automatically aligns with various industry compliance standards. This misleadingly suggests a “set it and forget it” approach, while in reality, achieving and maintaining compliance requires ongoing effort. The reality is that the out-of-the-box setup typically provides a baseline but not a guarantee of full compliance.
Compliance Standards and Endpoint Security
Numerous regulations and standards impact endpoint security. Examples include HIPAA for healthcare, GDPR for data protection, and PCI DSS for payment card security. These standards dictate specific requirements for data protection, access controls, and incident response, all of which need to be addressed in the endpoint security implementation. Each standard demands a tailored approach to configuration and management, often going beyond basic software installations.
Approaches to Achieving Compliance
Achieving compliance involves a multi-faceted approach. Initial configuration settings play a crucial role. These settings should be customized to meet the unique needs and requirements of the organization, taking into account the specific industry standards. Ongoing software updates are essential to address vulnerabilities and incorporate compliance updates. Furthermore, robust security policies, consistently enforced and monitored, are critical to ensuring adherence to standards.
Pitfalls of Claiming Compliance “Out of the Box”
Claiming compliance “out of the box” without thorough verification and testing is a significant pitfall. This often results in a false sense of security. Organizations may be exposed to compliance violations or hefty penalties. Without a detailed assessment, critical gaps in security posture can remain undetected, potentially leading to security breaches. A critical approach requires regular compliance assessments and audits to validate the actual level of compliance.
Automated Compliance Posture Assessments vs. Manual Audits
Automated compliance posture assessments offer a streamlined way to evaluate endpoint security against compliance standards. These assessments often utilize pre-defined criteria to identify compliance gaps. While automated tools are invaluable, they should not replace manual audits. Manual audits provide a more in-depth and nuanced understanding of the security posture, including the context of individual endpoints and the potential impact of specific configurations.
Manual audits allow for a deeper analysis of complex scenarios.
Endpoint security’s biggest issue often boils down to claiming compliance “out of the box,” a misleading promise. While tools like HubSpot and AI-powered CRM solutions like HubSpot and AI smarter CRM solutions focus on streamlined processes and intelligent automation, endpoint security still struggles to deliver genuine, customized compliance solutions. This often leads to a lot of extra work for IT teams trying to get the security right.
Ultimately, true compliance needs careful configuration, not just a pre-packaged claim.
Common Issues with “Out of the Box” Endpoint Security Compliance Claims
The promise of “out-of-the-box” compliance in endpoint security solutions often masks significant complexities. Vendors frequently overstate the extent to which their products meet regulatory requirements without adequate consideration for diverse environments and real-world configurations. This often leads to false assumptions and ultimately, vulnerabilities.Vendors often rely on pre-configured settings and default policies, which may not address the unique needs and risks of specific organizations.
While these initial settings might appear compliant, they frequently fail to adapt to evolving threats, regulatory updates, and unique organizational structures. This leaves the door open to security gaps and compliance violations.
Inadequate Patching and Update Mechanisms
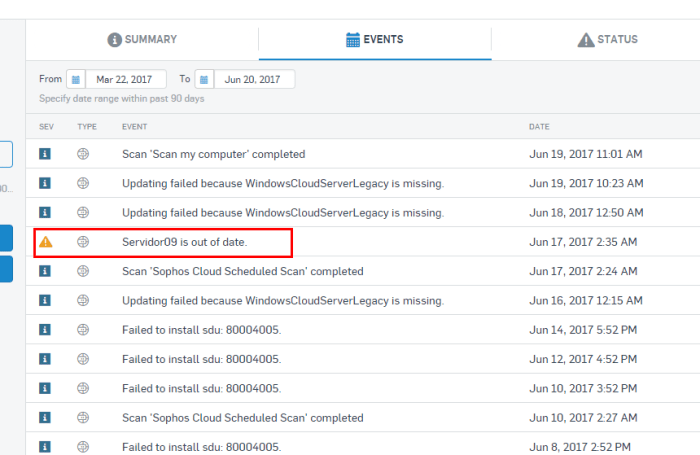
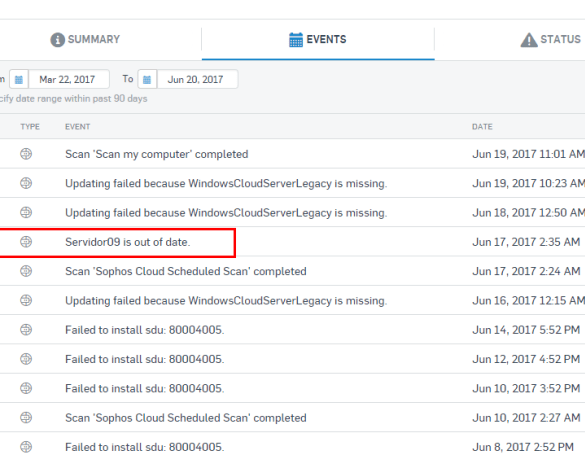
A critical factor impacting “out-of-the-box” compliance is the effectiveness of patching and update mechanisms. While vendors might claim initial compliance, their products often rely on scheduled or automatic updates that may not be sufficient in rapidly evolving threat landscapes. This can lead to security vulnerabilities remaining unpatched for extended periods. Furthermore, the speed and reliability of update deployment across a large enterprise network can significantly impact compliance posture.
Poor update mechanisms can leave devices exposed to known exploits, ultimately violating compliance standards.
Endpoint security often falsely claims compliance out of the box, a major problem. Businesses need to be careful about this, especially when it comes to local service businesses, which need strong SEO strategies to attract customers. A good local service business SEO strategy can help a business stand out, but even with the best SEO, robust endpoint security procedures are still crucial for maintaining compliance.
This means going beyond the basic claims and implementing comprehensive checks to ensure true security, not just superficial compliance.
Configuration Drift
Configuration drift, a significant concern in endpoint security, arises from the dynamic nature of IT environments. While an initial configuration might be compliant, modifications, additions, or even accidental changes can erode this compliance over time. This drift is often undetected, allowing vulnerabilities to creep into the system. The need for continuous monitoring and automated remediation is crucial to maintaining compliance posture.
Potential Security Misconfigurations
Despite claims of “out-of-the-box” compliance, pre-configured settings may contain security misconfigurations. For instance, default firewall rules might allow unauthorized access, or unnecessary services might be enabled, creating vulnerabilities. These issues, often overlooked in the initial assessment, are critical to identify and mitigate to ensure long-term compliance. Vendors must proactively address these issues through robust default configurations and comprehensive documentation.
Examples of Security Vulnerabilities
A common example involves default firewall rules that allow inbound connections from untrusted networks. This may seem compliant initially but exposes systems to potential malicious attacks. Another example is the lack of timely updates for known vulnerabilities. This can leave endpoints susceptible to exploitation, even with a “compliant” initial configuration. The absence of robust security awareness training for administrators can also contribute to configuration drift and misconfigurations, impacting overall compliance posture.
Impact of False Compliance Claims
False claims of “out-of-the-box” endpoint security compliance can have devastating consequences for organizations. These claims, often made to attract customers or meet regulatory requirements, can mask underlying vulnerabilities and expose businesses to significant risks. A seemingly simple marketing pitch can quickly unravel into a complex web of legal and reputational issues.Organizations that misrepresent their endpoint security posture risk severe penalties and damage their standing in the market.
The trust of customers and partners can be eroded, leading to lost revenue and market share. Understanding the potential negative impacts of false compliance claims is critical for businesses looking to build a strong and secure IT infrastructure.
Negative Consequences for Organizations
False compliance claims can lead to a cascade of negative outcomes for organizations. The consequences aren’t just limited to reputational damage; they can have substantial financial and legal ramifications.
- Damaged Reputation and Brand Image: A single incident of a false compliance claim can significantly harm an organization’s reputation. Loss of customer trust and reduced brand value can be long-lasting. For example, a major retailer falsely claiming compliance with stringent data protection regulations could lose the trust of consumers, impacting sales and market share.
- Legal Liabilities and Financial Penalties: Misrepresenting compliance can expose an organization to significant legal liabilities. This includes regulatory fines, lawsuits from customers or partners who have suffered damages, and potential criminal charges in severe cases. A financial institution misrepresenting its security posture in the face of a data breach could face not only regulatory penalties but also potentially billions of dollars in customer redress.
- Regulatory Fines or Penalties for Non-Compliance: Even if an organization doesn’t actively misrepresent its compliance, a lack of true compliance can trigger regulatory fines or penalties. For instance, if a healthcare provider fails to meet HIPAA compliance requirements, they face potential penalties of hundreds of thousands of dollars, and even more, depending on the severity and duration of the non-compliance.
- Data Breaches: False claims of compliance often mask underlying vulnerabilities in an organization’s endpoint security. These vulnerabilities can be exploited by malicious actors, leading to data breaches and significant financial losses. A company that claims robust security measures but lacks proper implementation of security controls is susceptible to breaches, leading to the theft of sensitive data, reputational damage, and potentially hefty fines from regulatory bodies.
Financial Impact of False Claims
The financial implications of false compliance claims can be substantial. Beyond the immediate costs of regulatory fines and legal fees, there are often hidden costs associated with damage to reputation and lost opportunities.
- Direct Financial Losses: Fines and legal settlements associated with non-compliance can cripple an organization’s finances. In extreme cases, these losses can be insurmountable, leading to bankruptcy. A company found guilty of false compliance claims can face hefty fines and legal costs that significantly impact their bottom line.
- Indirect Financial Losses: Loss of customer trust, reduced brand value, and decreased market share can have a significant impact on future revenue. Companies with damaged reputations struggle to attract new customers and maintain existing ones. A manufacturer of medical equipment falsely claiming compliance with relevant regulations could lose customers and face significant future losses.
Evaluating Endpoint Security Compliance Posture: Endpoint Security S Biggest Issue Claiming Compliance Out Of The Box
Beyond the initial claims of “compliance out of the box,” a crucial step in securing endpoint devices is rigorous evaluation of their actual security posture. This involves a systematic approach to verifying that the deployed security solutions effectively meet the requirements of chosen compliance standards. A thorough assessment goes beyond a simple checklist and delves into the nuances of implementation and configuration.
Structured Method for Evaluating Compliance
A structured method for evaluating endpoint security solutions focuses on a multi-faceted approach. It begins with clearly defined objectives, considering specific compliance standards and relevant regulations. This method should include a documented process, with clear roles and responsibilities for each step. Regular audits and reviews are essential to ensure continuous compliance and identify any emerging vulnerabilities.
Checklist for Assessing Endpoint Security Posture, Endpoint security s biggest issue claiming compliance out of the box
A comprehensive checklist helps streamline the assessment process. This checklist should cover all critical aspects of endpoint security, including but not limited to: operating system patching, antivirus software, firewall configurations, user access controls, data encryption, and device hardening. Regular updates to the checklist are necessary to adapt to evolving threats and compliance standards.
- Operating System Patches: Verify the presence of the latest security patches on all endpoint devices. Out-of-date systems are significant vulnerabilities. Failure to update systems creates pathways for exploits.
- Antivirus Software: Confirm the active installation and up-to-date signature databases for all endpoint protection solutions. Malware definitions are critical for effective threat detection. Outdated definitions can leave devices vulnerable to attacks.
- Firewall Configurations: Review firewall rules and configurations to ensure they comply with security policies and block unauthorized network access. Comprehensive firewall rules are essential for perimeter protection. Inconsistent firewall rules can expose devices to intrusions.
- User Access Controls: Evaluate user access privileges to restrict access to sensitive data and resources based on the principle of least privilege. Strict access controls limit the impact of a security breach. Lack of access control can allow unauthorized users to gain access to sensitive data.
- Data Encryption: Verify that sensitive data is encrypted at rest and in transit. Encryption protects data confidentiality. Without encryption, data breaches can expose sensitive information.
- Device Hardening: Assess the security settings and configurations of endpoint devices to prevent unauthorized access and malware infections. Hardening reduces the attack surface of endpoint devices. Weak hardening allows attackers to exploit vulnerabilities.
Compliance Standards Verification
Verification of compliance requires understanding the specific requirements of each applicable standard. A table outlining different compliance standards and corresponding verification steps is crucial for efficient assessment.
| Compliance Standard | Verification Steps |
|---|---|
| HIPAA | Verify encryption of protected health information (PHI), access controls, and audit logs. |
| PCI DSS | Validate data encryption, secure network configurations, and vulnerability management. |
| NIST Cybersecurity Framework | Assess risk management, incident response, and security controls based on defined criteria. |
| GDPR | Ensure data protection, user consent, and data breach notification procedures. |
Using Vulnerability Scanning Tools
Automated vulnerability scanning tools are indispensable for identifying compliance gaps. These tools provide a comprehensive view of potential weaknesses in endpoint configurations. Regular scans are crucial to maintain a secure posture.
Vulnerability scanning tools identify misconfigurations, missing patches, and known vulnerabilities that might not be immediately apparent during manual checks.
Using tools like Nessus, OpenVAS, or Qualys, organizations can automate the identification of compliance gaps and prioritize remediation efforts. These tools are crucial in proactively managing risk.
Configuring Security Policies
Implementing and configuring security policies that align with compliance standards is a critical aspect of maintaining a secure endpoint posture. Policies must be clearly defined, regularly reviewed, and effectively communicated to all users. This includes clear procedures for incident response, data breach notification, and user training.
Security policies should be specific, measurable, achievable, relevant, and time-bound (SMART) to ensure effective implementation.
Implementing these policies ensures that all endpoint devices are consistently protected and compliant with regulations.
Best Practices for Genuine Endpoint Security Compliance
The proliferation of endpoint devices and the ever-evolving threat landscape have made achieving genuine endpoint security compliance a significant challenge. Simply claiming compliance “out of the box” is insufficient; organizations must implement robust processes and technologies to ensure their endpoints are secure and aligned with industry standards. This requires a proactive and multifaceted approach that goes beyond basic configurations.Achieving genuine endpoint security compliance necessitates a shift from a reactive to a proactive security posture.
This involves a comprehensive strategy that encompasses security audits, proactive monitoring, employee training, and the selection of appropriate tools and technologies. Compliance is not a one-time event but a continuous process demanding ongoing attention and adaptation to new threats.
Regular Security Audits and Assessments
Regular security audits and assessments are crucial for identifying vulnerabilities and ensuring that security controls are effectively implemented. These audits should cover all aspects of endpoint security, including access controls, patch management, and security configurations. The assessment process should include both automated tools and manual reviews to provide a comprehensive picture of the security posture. A regular audit schedule, say, quarterly or annually, ensures that security controls remain aligned with the latest threats and industry best practices.
Proactive Security Monitoring and Threat Detection
Proactive security monitoring and threat detection are essential for identifying and responding to threats before they impact sensitive data. This involves continuously monitoring endpoint activities for suspicious patterns and anomalies. Implement systems that can detect and alert on potential threats in real-time, allowing organizations to respond quickly and contain any breaches. The information gathered from monitoring should be analyzed to identify trends and improve the overall security posture.
Security Awareness Training for Employees
Employee training is a critical component of a robust endpoint security strategy. Employees often represent the weakest link in the security chain. Providing regular security awareness training can equip them with the knowledge and skills to identify and avoid phishing attempts, malware infections, and other security threats. The training should be tailored to the specific roles and responsibilities of employees and should be updated regularly to reflect emerging threats.
Tools and Technologies for Maintaining Compliance
Numerous tools and technologies can aid in maintaining compliance with endpoint security standards. These include endpoint detection and response (EDR) solutions, intrusion detection and prevention systems (IDS/IPS), and vulnerability management tools. Selecting the appropriate tools requires careful consideration of the specific needs and resources of the organization. These tools should be integrated seamlessly into the existing infrastructure to ensure effective threat detection and response.
For example, a robust SIEM (Security Information and Event Management) system can aggregate logs from various sources, providing a centralized view of security events and enabling proactive threat hunting.
Endpoint security often struggles with the false claim of “compliance out of the box.” Understanding your target audience, like in a display campaign (check out the anatomy of a display campaign target audience ), is crucial. If you don’t precisely tailor your security measures to your specific user base, the “out-of-the-box” approach is likely to fall short of true compliance, leaving your endpoint vulnerable.
Case Studies of Endpoint Security Compliance Failures
Relying on “out-of-the-box” endpoint security solutions for compliance can be tempting, but often leads to costly mistakes. This section delves into real-world examples of organizations that fell victim to this trap, highlighting the causes of their failures and the severe consequences. Understanding these case studies is crucial for avoiding similar pitfalls and ensuring genuine compliance.Organizations often assume that simply installing endpoint security software guarantees regulatory compliance.
However, this is a dangerous oversimplification. True compliance requires a deep understanding of the specific regulations and a comprehensive implementation strategy. The following case studies demonstrate the potential for significant problems when organizations neglect these critical details.
Examples of Organizations Experiencing Compliance Issues
Numerous organizations have faced compliance challenges by solely relying on default endpoint security settings. These issues can stem from various factors, including inadequate configuration, lack of proper training, and insufficient ongoing monitoring.
- A healthcare provider, prioritizing speed over security, implemented an endpoint security solution without customizing its settings to comply with HIPAA regulations. The default configuration lacked critical features for protecting sensitive patient data, leading to a vulnerability that was exploited. The breach resulted in substantial fines and reputational damage.
- A financial institution, eager to streamline their security posture, relied on the “out-of-the-box” capabilities of their endpoint security platform to meet PCI DSS requirements. However, their solution lacked the granular controls needed to meet specific PCI DSS criteria for secure payment processing. The deficiency was detected during an audit, resulting in significant financial penalties and the loss of customer trust.
- A government agency, focused on minimizing initial costs, chose an endpoint security solution with limited reporting capabilities. The limited visibility into endpoint activity made it difficult to track and respond to security incidents, leading to a failure to comply with relevant government regulations and ultimately a costly data breach.
Causes of Compliance Failures
The root causes of these compliance failures are often interconnected. A lack of comprehensive security policies, insufficient staff training, and inadequate ongoing monitoring can create a perfect storm for regulatory violations. Moreover, the complexity of modern regulations, and the evolving nature of cyber threats, demand more than simply selecting a product and expecting compliance.
- Lack of a tailored security policy: A crucial element often missing is a clear, well-defined security policy that Artikels the specific compliance requirements for endpoint security. This policy should be consistently reviewed and updated to adapt to changing threats and regulatory landscapes.
- Inadequate staff training: Employees must be trained on the proper use and configuration of endpoint security software, and how to respond to security alerts. Regular training sessions are essential to maintain a strong security posture.
- Insufficient ongoing monitoring: Implementing regular monitoring and reporting tools is crucial to detect and respond to security threats promptly. This enables the timely identification of potential vulnerabilities and ensures ongoing compliance.
Regulatory Penalties from False Compliance Claims
The consequences of false compliance claims can be severe. Organizations that are found to be non-compliant can face significant regulatory penalties, substantial financial losses, and damage to their reputation. It is vital to ensure the security measures are thoroughly implemented and validated against the relevant regulatory framework.
- Many regulatory bodies, such as the Federal Trade Commission (FTC) in the US and the Information Commissioner’s Office (ICO) in the UK, have the authority to impose substantial fines for violations of data protection regulations.
- These penalties often reflect the severity of the data breach, the extent of the damage, and the organization’s failure to implement appropriate security measures.
- Organizations that make false compliance claims risk not only fines but also damage to their reputation and loss of customer trust.
Lessons Learned and Preventive Measures
These case studies underscore the importance of a proactive and comprehensive approach to endpoint security compliance. Simply selecting an “out-of-the-box” solution is insufficient. A robust security strategy requires thorough planning, ongoing monitoring, and a deep understanding of the specific regulatory requirements.
- Implement a detailed security policy outlining the specific requirements for endpoint security.
- Provide thorough training to employees on the use and configuration of endpoint security tools.
- Establish robust monitoring and reporting processes to detect and respond to security incidents promptly.
- Conduct regular security audits to validate the effectiveness of the security controls and ensure compliance.
Technical Considerations for Endpoint Security Compliance
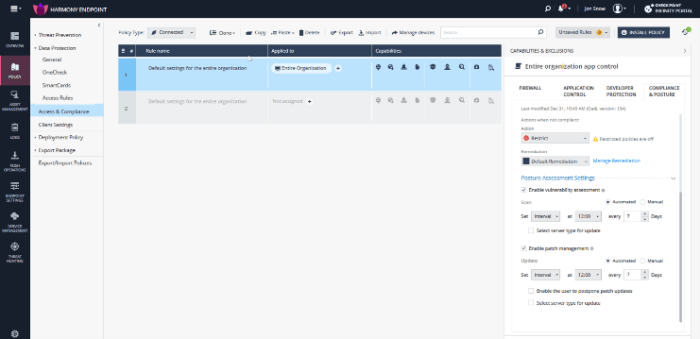
Ensuring endpoint security solutions meet compliance requirements demands a deep dive into the technical aspects of implementation and configuration. This goes beyond simply installing software; it involves meticulous planning, precise configuration, and continuous monitoring to maintain a robust security posture. The technical considerations Artikeld here provide a roadmap for organizations seeking to achieve and maintain compliance.The technical landscape of endpoint security is constantly evolving, requiring organizations to stay abreast of emerging threats and vulnerabilities.
Solutions must be adaptable and resilient to meet the ever-changing compliance standards and regulatory frameworks.
Configuration Requirements for Security Controls
Implementing various security controls requires careful configuration to ensure effectiveness and compliance. Each control, from firewalls to intrusion detection systems (IDS), needs to be correctly configured to achieve the desired security outcomes. Misconfigurations can lead to significant vulnerabilities, compromising compliance efforts.
- Firewall Configuration: Firewalls must be configured to allow only authorized traffic while blocking potentially malicious connections. This involves defining inbound and outbound rules based on specific applications, protocols, and network segments. Careful consideration of permitted ports and protocols is critical for compliance.
- Intrusion Detection/Prevention Systems (IDS/IPS): IDS/IPS systems must be properly configured to identify and respond to malicious activity. Defining signatures and rules to detect known threats, as well as anomalies, is crucial. False positives must be mitigated to avoid unnecessary disruptions to legitimate traffic.
- Antivirus/Antimalware: Antivirus/antimalware solutions need to be updated regularly and configured to scan files, applications, and processes in real-time. Custom exclusions for legitimate applications are necessary to avoid disruptions to business operations. Scanning frequency and behavior monitoring are vital.
Endpoint Security Solution Comparison
A comparative analysis of endpoint security solutions is vital for selecting the right toolset for compliance needs. Different solutions cater to varying security requirements, so understanding their strengths and weaknesses regarding compliance capabilities is crucial.
| Endpoint Security Solution | Compliance Capabilities | Configuration Complexity | Cost |
|---|---|---|---|
| Solution A | Excellent support for industry standards like NIST, ISO 27001 | Medium | High |
| Solution B | Good support for common standards, but limited customizability | Low | Medium |
| Solution C | Basic support for industry standards, requires extensive configuration | High | Low |
Configuring Security Policies for Maximum Protection and Compliance
Security policies form the backbone of any endpoint security strategy. Policies dictate how the security controls operate, ensuring compliance with established guidelines. Effective policies encompass access controls, user permissions, and incident response protocols.
- Access Controls: Policies must clearly define user access rights and permissions to sensitive data and systems, minimizing potential vulnerabilities. Granular access controls are critical to prevent unauthorized access and data breaches.
- User Permissions: Policies should define roles and permissions for users based on their job functions. This restricts access to only necessary resources and prevents unauthorized actions.
- Incident Response: Policies must clearly Artikel procedures for handling security incidents. This includes reporting mechanisms, containment strategies, and remediation steps. Quick response is vital to mitigate damage and maintain compliance.
Regular Updates and Patches for Maintaining Compliance
Regular updates and patches are essential for maintaining compliance. Vulnerabilities are constantly being discovered and exploited, so keeping security software up-to-date is crucial. Patch management is a critical component of ongoing compliance efforts.Regular updates mitigate known vulnerabilities, improving the overall security posture and reducing the risk of exploitation. Automated patch management tools are crucial for efficiency and minimizing manual effort.
A documented patch management process is critical for compliance.
Final Conclusion
In conclusion, relying on “out-of-box” compliance claims in endpoint security is a risky proposition. Organizations must move beyond superficial promises and prioritize genuine compliance verification. This involves a proactive approach that includes regular audits, assessments, and a commitment to maintaining up-to-date security policies. By adopting a more comprehensive and diligent approach, businesses can safeguard their data, reputation, and financial well-being.
Let’s ensure that endpoint security solutions truly deliver on their compliance promises.